Encrypt And Decrypt Using The Existing Aes Which Uses Key Addition

Encrypt And Decrypt Using The Existing Aes Which Uses Key Addition Encryption is a process that converts plaintext data into a coded format, making it unreadable without the correct decryption key. this essential security measure protects sensitive information from unauthorized access, ensuring that your files remain private and secure. In cryptography, encryption (more specifically, encoding) is the process of transforming information in a way that, ideally, only authorized parties can decode. this process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext.

Encryption And Decryption Using The Existing Aes Which Uses Key Give our universal encrypt decrypt tool a try! encrypt or decrypt any string using various algorithm with just one mouse click. aes (advanced encryption standard) is the most popular encryption algorithm out of the ones we have listed. The primary purpose of encryption is to protect the confidentiality of digital data stored on computer systems or transmitted over the internet or other computer networks. it is used to safeguard a wide range of data, from pii to sensitive corporate assets to government and military secrets. Encryption is the process of converting or scrambling data into an unreadable, encoded version that can only be read with authorized access to a decryption key. Encryption converts sensitive information or data into a secret code to prevent unauthorized access. if you’ve ever made an online purchase, logged in to your social media accounts, or filled out an online contact form, your information already exists as encrypted data.

Pdf Advanced Encryption Standard Aes Algorithm To Encrypt And Encryption is the process of converting or scrambling data into an unreadable, encoded version that can only be read with authorized access to a decryption key. Encryption converts sensitive information or data into a secret code to prevent unauthorized access. if you’ve ever made an online purchase, logged in to your social media accounts, or filled out an online contact form, your information already exists as encrypted data. Learn what encryption is, how it works, and explore real world examples in this guide. understand the basics to safeguard your data and privacy. Encryption is a way to scramble data so that only authorized parties can unscramble it. learn about how encryption works and why encryption is important. Encryption is a crucial technology for digital security, ensuring privacy by changing data into unreadable form for those without access. historical encryption techniques like the scytale, polybius square, and caesar's cipher have influenced modern encryption systems. Meaning of encrypt, its purpose, types, and importance in data security. learn about encryption methods, algorithms, and their role in protecting information.

Image Encryption Using Aes Key Expansion Ppt Learn what encryption is, how it works, and explore real world examples in this guide. understand the basics to safeguard your data and privacy. Encryption is a way to scramble data so that only authorized parties can unscramble it. learn about how encryption works and why encryption is important. Encryption is a crucial technology for digital security, ensuring privacy by changing data into unreadable form for those without access. historical encryption techniques like the scytale, polybius square, and caesar's cipher have influenced modern encryption systems. Meaning of encrypt, its purpose, types, and importance in data security. learn about encryption methods, algorithms, and their role in protecting information.

Image Encryption Using Aes Key Expansion Ppt Encryption is a crucial technology for digital security, ensuring privacy by changing data into unreadable form for those without access. historical encryption techniques like the scytale, polybius square, and caesar's cipher have influenced modern encryption systems. Meaning of encrypt, its purpose, types, and importance in data security. learn about encryption methods, algorithms, and their role in protecting information.
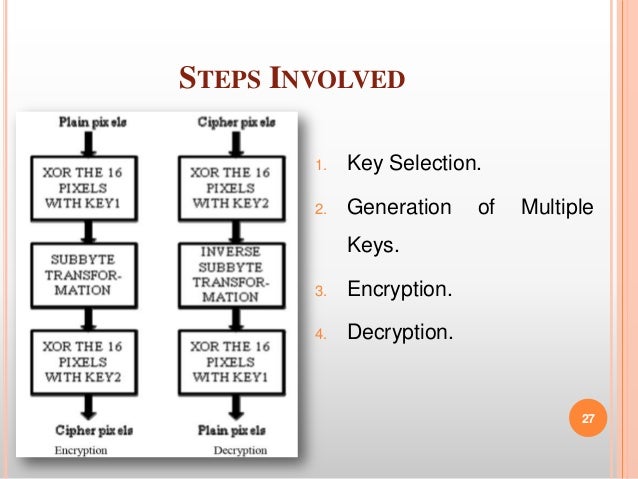
Image Encryption Using Aes Key Expansion
Comments are closed.