Detecting Cleared Event Logs Using Log360
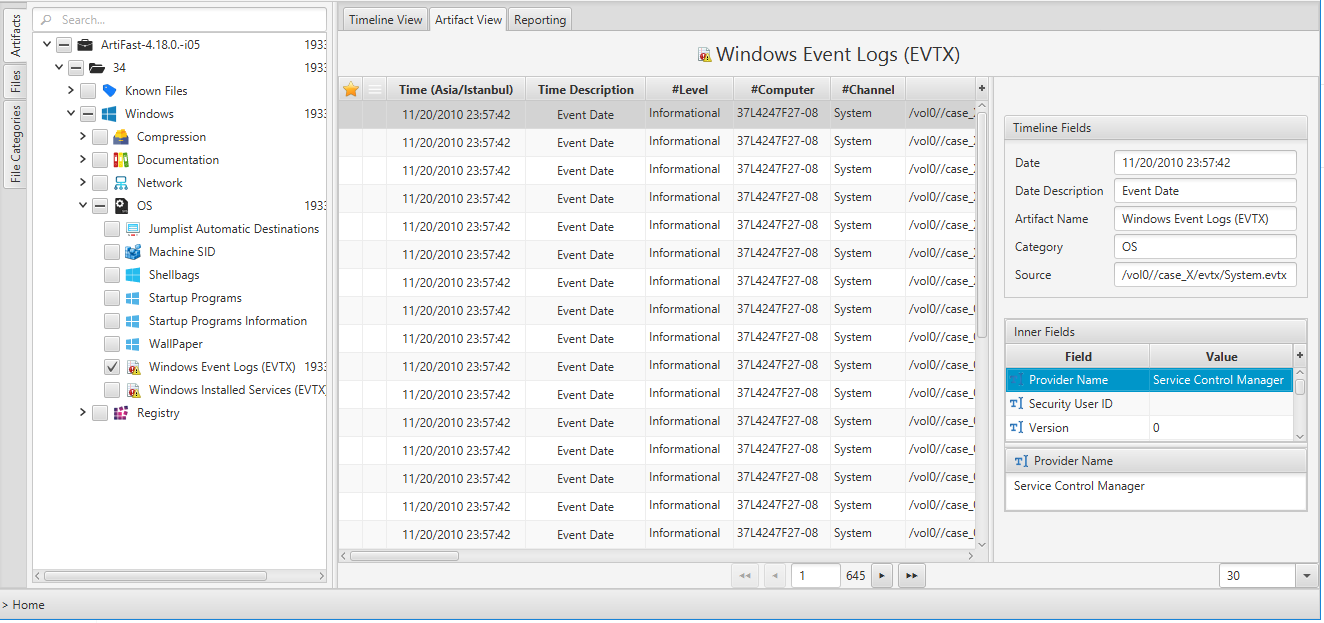
Windows Event Logs In this video, we explore how cybercriminals execute this attack and how our unified siem solution, manageengine log360, helps detect and respond to it. Log360 analyzes log data in real time from multiple sources in your environment and delivers a detailed event timeline for each detected incident, enabling you to get in depth information on compromised accounts, infected devices, and more.
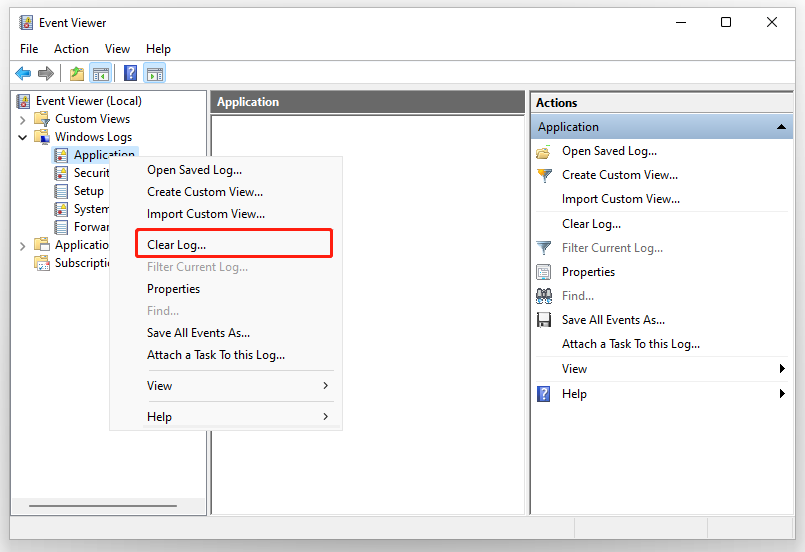
Clear Windows Event Viewer Logs It Support Perth 0415 920 471 To effectively use log360, collect logs from various sources to gain a complete view of your it environment. logs are easily analyzed using dashboards with graphs and reports, helping to identify security threats, detect unusual activities, and mitigate risks early. Correlate log data collected from heterogeneous sources to detect attack patterns instantly using log360's real time event correlation engine. get notified immediately via email sms when any suspicious activity occurs in the network. I've inherited a siem log360 ela adaudit plus. this doesn't seem to be the best possible option out there, but i think it can qualify if configured well enough. How to automatically discover log sources in log360? no description has been added to this video.
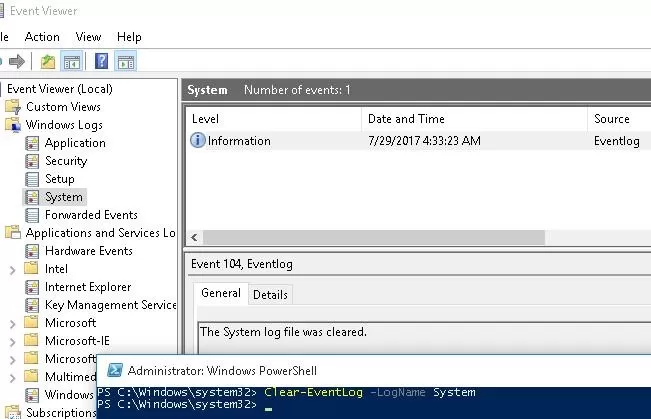
How To Clear Event Viewer Logs On Windows Windows Os Hub I've inherited a siem log360 ela adaudit plus. this doesn't seem to be the best possible option out there, but i think it can qualify if configured well enough. How to automatically discover log sources in log360? no description has been added to this video. A security information and event management (siem) solution like log360 aggregates, securely stores, and efficiently analyzes the log data generated by your network devices to detect treats and mitigate attacks. Once an intrusion is detected, you can investigate it further based on the source, destination, and severity. besides detection and analysis, you can automate your response to these events with workflows that can minimize critical response time during an attack. Imagine having to run from one network device to another to troubleshoot issues. sounds like a nightmare, right? this is where log360's auditing component can help. it can collect logs from all your network devices and applications, analyze them, and prepare reports based on the log data. The correlation engine discovers sequences of logs, coming from devices across your network, that indicate possible attacks, and quickly alerts you about the threat. building strong event log correlation and analysis capabilities empowers you to start taking proactive steps against network attacks.
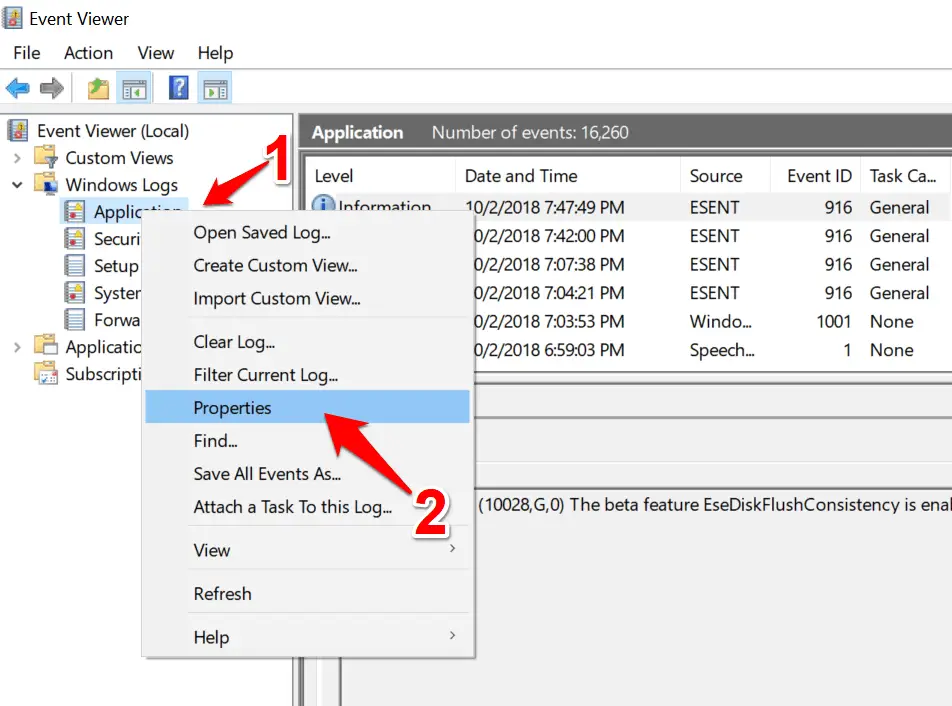
Clear All Event Logs In Event Viewer In Windows 10 Technical Ustad A security information and event management (siem) solution like log360 aggregates, securely stores, and efficiently analyzes the log data generated by your network devices to detect treats and mitigate attacks. Once an intrusion is detected, you can investigate it further based on the source, destination, and severity. besides detection and analysis, you can automate your response to these events with workflows that can minimize critical response time during an attack. Imagine having to run from one network device to another to troubleshoot issues. sounds like a nightmare, right? this is where log360's auditing component can help. it can collect logs from all your network devices and applications, analyze them, and prepare reports based on the log data. The correlation engine discovers sequences of logs, coming from devices across your network, that indicate possible attacks, and quickly alerts you about the threat. building strong event log correlation and analysis capabilities empowers you to start taking proactive steps against network attacks.
Comments are closed.