Deconstructing And Rewiring Bug Bounty Programs Cobalt
What Are Bug Bounty Programs Here S Everything You Need To Know Leading software companies such as google and facebook have all praised their public bug bounty programs. bug bounty platforms have advocated for launching such programs as well. at cobalt, we have worked with organizations to launch more than 200 bug bounty programs. We often are asked how’s the best way to work with incoming reports on a bug bounty program. below are some of the best practices we have found while running our own program.
Deconstructing And Rewiring Bug Bounty Programs Cobalt Explore the life of a cybersecurity bug with an insightful introduction of the find to fix pipeline from cobalt board member, jacob hansen. These marketplaces offer an online businesses the opportunity to easily start and manage their own bug bounty program, and leverage the power of the security community. explore the differences between a penetration test and bug bounty program. While bug bounty programs are sometimes appropriate, there are crowdsourced security alternatives which are often better suited in a range of situations. in the blog post deconstructing bug bounties, i compare and contrast some of these different approaches. With this post i'll present a way to better understand bugs, from their origin until their death. i’ll do this by introducing the idea of a security bug pipeline and fix to fix framework.
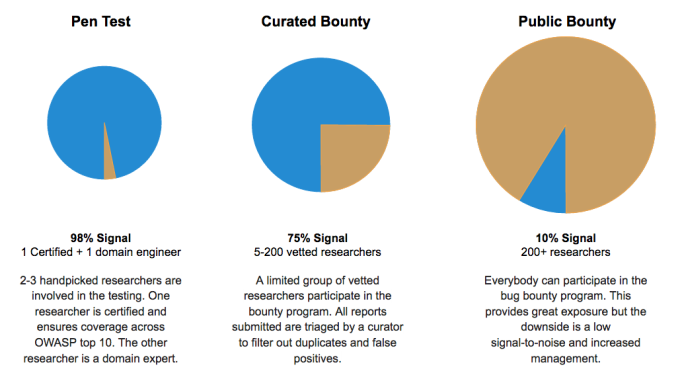
Deconstructing And Rewiring Bug Bounty Programs Cobalt While bug bounty programs are sometimes appropriate, there are crowdsourced security alternatives which are often better suited in a range of situations. in the blog post deconstructing bug bounties, i compare and contrast some of these different approaches. With this post i'll present a way to better understand bugs, from their origin until their death. i’ll do this by introducing the idea of a security bug pipeline and fix to fix framework. Bug bounties embrace a crowdsourced model for discovering application flaws. they reward researchers for disclosing flaws in a way that minimizes risk to the app, its data, and its users. …and they’re a bit chaotic. Please use dummy program one for testing on cobalt. you can create test vulnerabilities on the dummy program as part of your research. please target your own account when investigating a vulnerability. potential bugs related to rep are considered as low criticality. In our interview with friis jensen, he discussed the company’s beginning, including how cobalt.io developed its foundational bug bounty platform which allowed any company to run a bug bounty program. At cobalt, we have worked with organizations to launch more than 200 bug bounty programs. we have learned that there are significant management costs required to run a public bug bounty program.
Comments are closed.