Ddos Attack On A Virtual Machine Code Samples Microsoft Learn
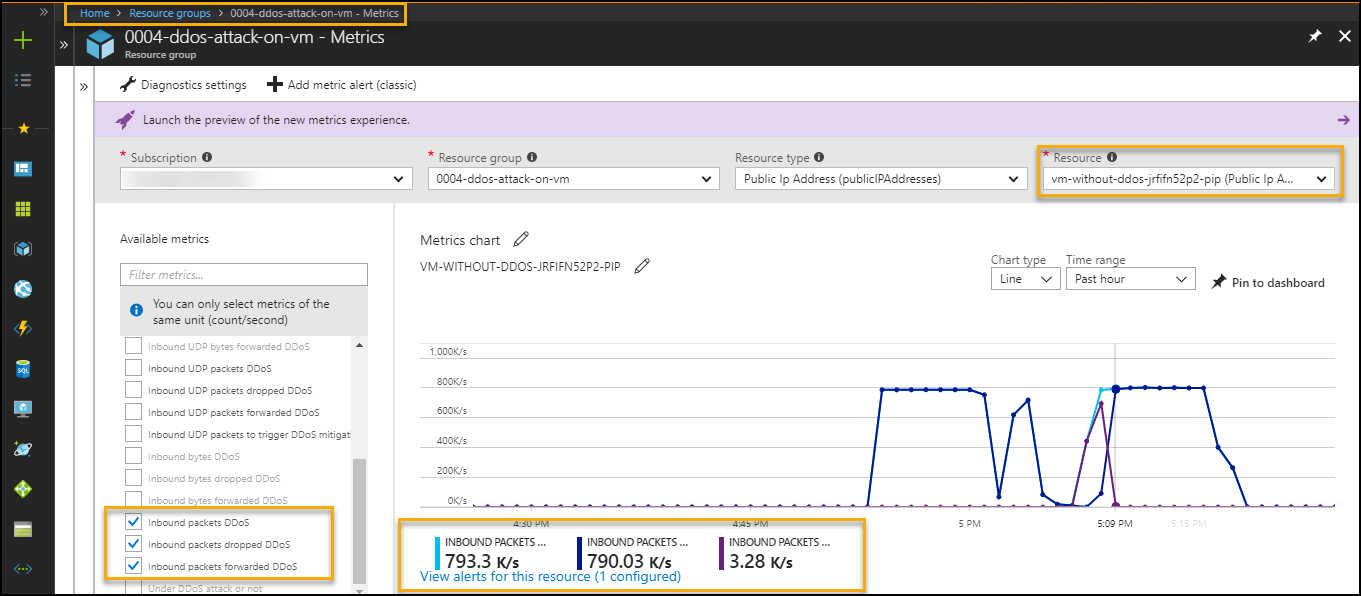
Ddos Attack On A Virtual Machine Code Samples Microsoft Learn # objective of the poc this playbook illustrates a simulated distributed denial of service (ddos) attack against a virtual machine. work through the configuration setting to enable ddos protections and get alerted when attacks occur. The following steps walk you through creating a virtual network, configuring ddos protection, and creating an attack which you can observe and monitor with the help of telemetry and metrics.
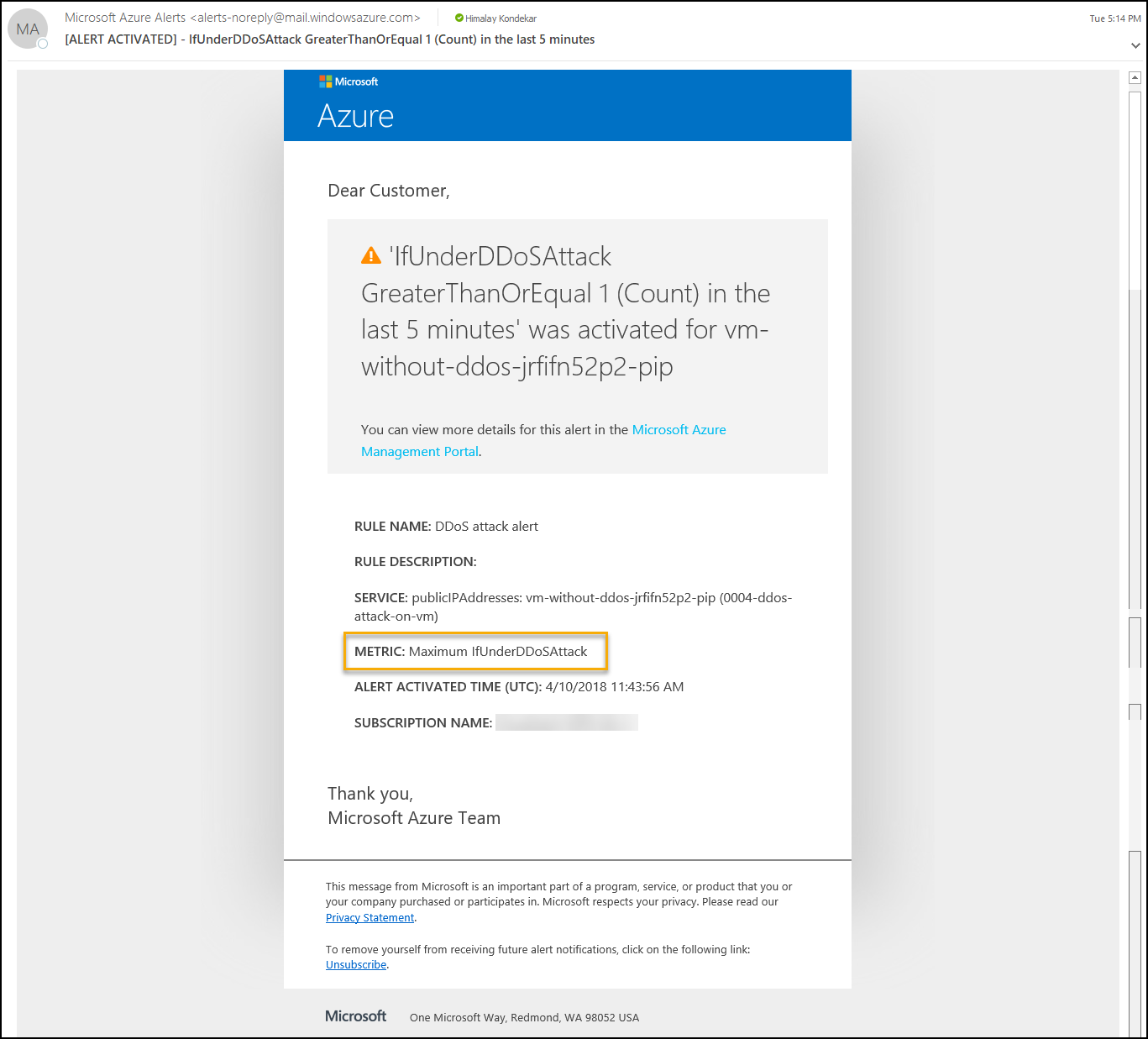
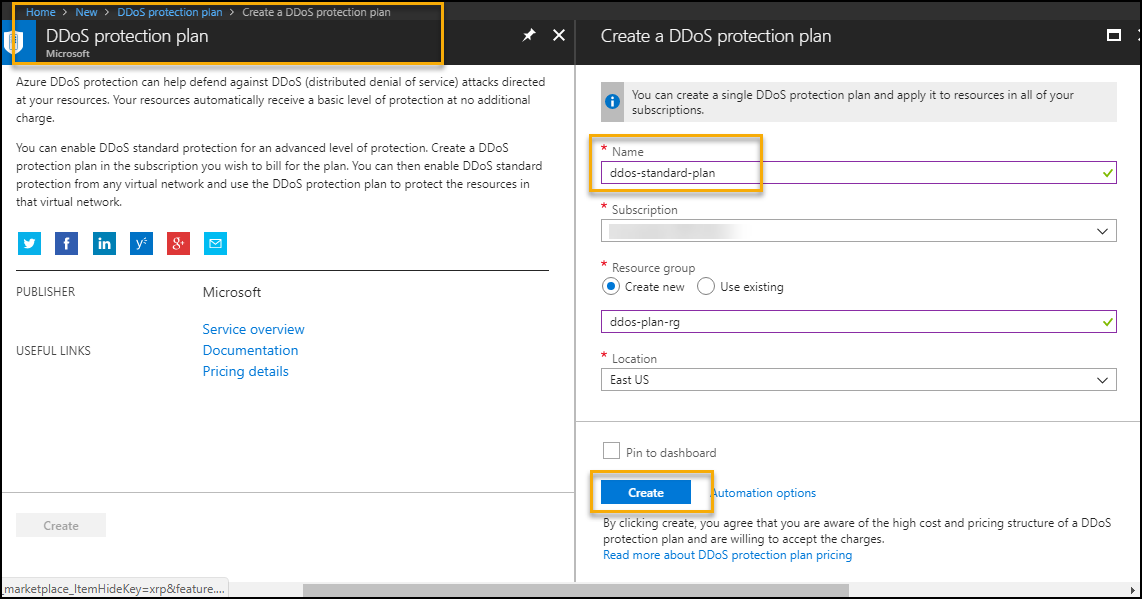
Ddos Attack On A Virtual Machine Code Samples Microsoft Learn Task 1: create a ddos protection plan. task 2: enable ddos protection on a new virtual network. task 3: configure ddos telemetry. task 4: configure ddos diagnostic logs. task 5: configure ddos alerts. task 6: monitor a ddos test attack. Microsoft have partnered with breakingpoint cloud to offer tooling for azure customers to generate traffic load against ddos protection enabled public endpoints to simulate tcp syn flood and dns flood attack on the vm without ddos protection standard. "one type of pen test that you can’t perform is any kind of denial of service (dos) attack. this test includes initiating a dos attack itself, or performing related tests that might determine, demonstrate, or simulate any type of dos attack.". This template creates a ddos protection plan and a virtual network. it also enables the ddos protection plan for the virtual network.

Ddos Attack On A Virtual Machine Code Samples Microsoft Learn "one type of pen test that you can’t perform is any kind of denial of service (dos) attack. this test includes initiating a dos attack itself, or performing related tests that might determine, demonstrate, or simulate any type of dos attack.". This template creates a ddos protection plan and a virtual network. it also enables the ddos protection plan for the virtual network. The following steps walk you through creating a virtual network, configuring ddos protection, and creating an attack which you can observe and monitor with the help of telemetry and metrics. Here are the main takeaways for this lab. a ddos attack is a malicious attempt to overwhelm an application's resources, making the application unavailable to legitimate users. azure ddos protection defends against ddos attacks. Learn how the azure ddos protection, when combined with application design best practices, provides defense against ddos attacks. This playbook illustrates a simulated distributed denial of service (ddos) attack against a virtual machine. work through the configuration setting to enable ddos protections and get alerted when attacks occur.

Ddos Attack On A Virtual Machine Code Samples Microsoft Learn The following steps walk you through creating a virtual network, configuring ddos protection, and creating an attack which you can observe and monitor with the help of telemetry and metrics. Here are the main takeaways for this lab. a ddos attack is a malicious attempt to overwhelm an application's resources, making the application unavailable to legitimate users. azure ddos protection defends against ddos attacks. Learn how the azure ddos protection, when combined with application design best practices, provides defense against ddos attacks. This playbook illustrates a simulated distributed denial of service (ddos) attack against a virtual machine. work through the configuration setting to enable ddos protections and get alerted when attacks occur.
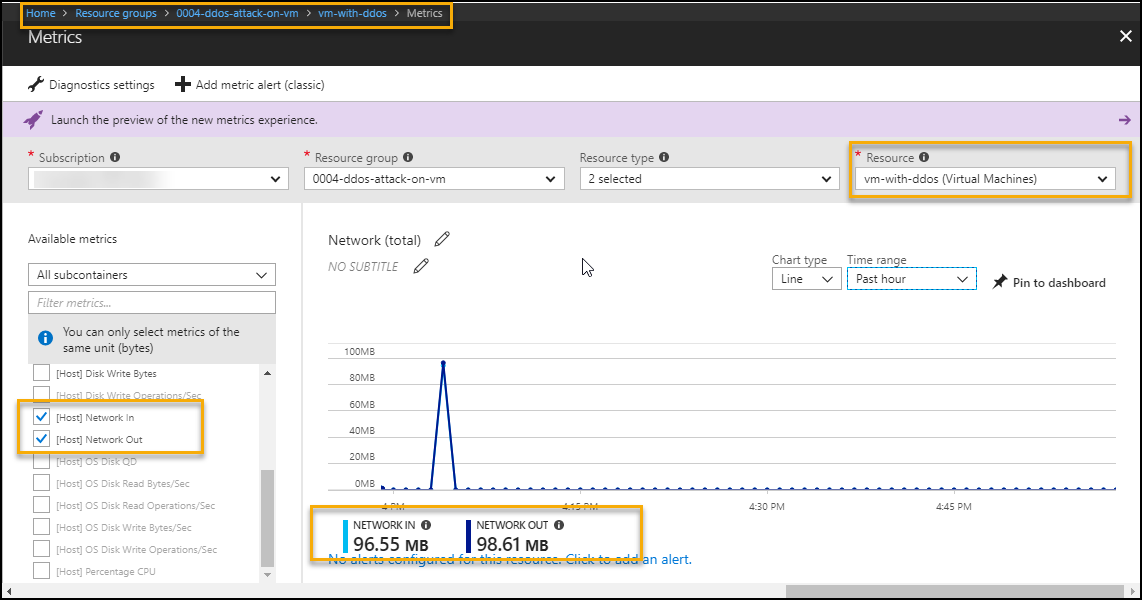
Ddos Attack On A Virtual Machine Code Samples Microsoft Learn Learn how the azure ddos protection, when combined with application design best practices, provides defense against ddos attacks. This playbook illustrates a simulated distributed denial of service (ddos) attack against a virtual machine. work through the configuration setting to enable ddos protections and get alerted when attacks occur.
Ddos Attack On A Virtual Machine Code Samples Microsoft Learn
Comments are closed.