Cryptography Pdf Public Key Cryptography Cryptography

Public Key Cryptography Pdf Public Key Cryptography Encryption Carefully written to communicate the major ideas and techniques of public key cryp tography to a wide readership, this text is enlivened throughout with historical remarks and insightful perspectives on the development of the subject. In this section, we explore public key encryption and the rsa encryption algorithm, named after the algorithm's inventors ron rivest, adi shamir, and len adleman.
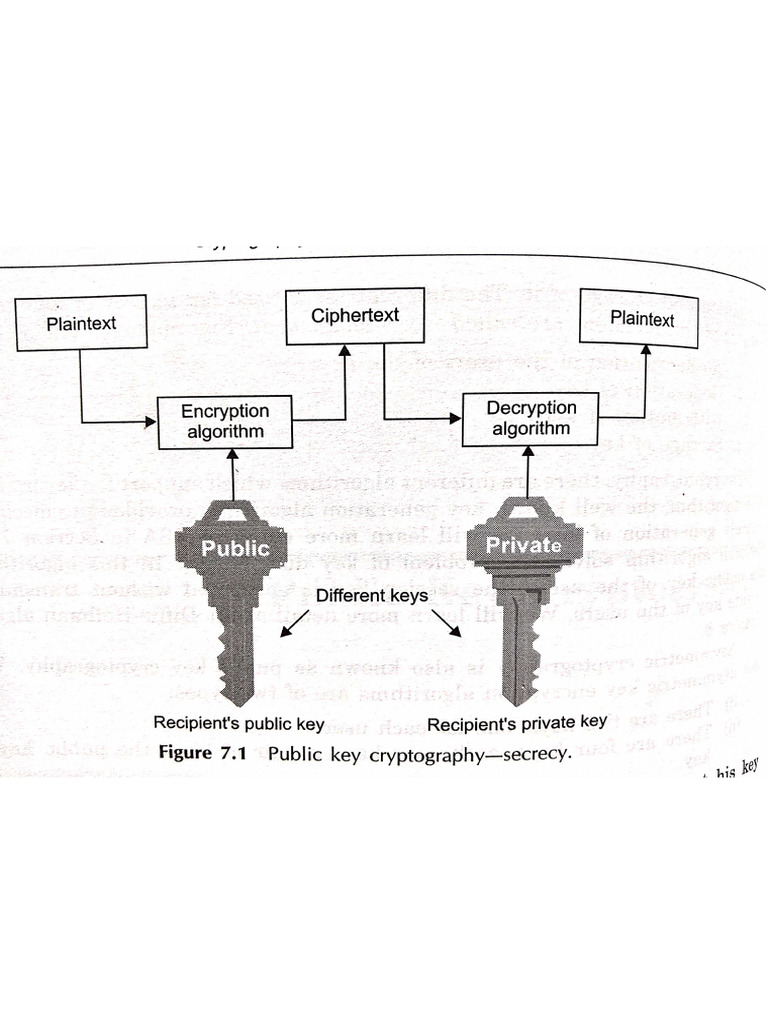
Public Key Cryptography Pdf – introduction to public key cryptography october 6, 2024 these slides were originally prepared by timo kasper and christof paar. later, they were modified by tomas fabsic for purposes of teaching i zkry at fei stu. Cryptanalysis is the study of techniques for breaking cryptographic systems. cryptanalysis is useful for strengthening cryptographic primitives. maintaining security and privacy is an ancient and primitive need. particularly relevant for military and diplomatic applications. Reduce protection of information to protection of authenticity of public keys • no need to keep public keys secret, but must be sure that alice’s public key is really her true public key. Each receiver possesses a unique decryption key, generally referred to as his private key. receiver needs to publish an encryption key, referred to as his public key. some assurance of the authenticity of a public key is needed in this scheme to avoid spoofing by adversary as the receiver.

Certificateless Public Key Cryptography A Research Survey Pdf Reduce protection of information to protection of authenticity of public keys • no need to keep public keys secret, but must be sure that alice’s public key is really her true public key. Each receiver possesses a unique decryption key, generally referred to as his private key. receiver needs to publish an encryption key, referred to as his public key. some assurance of the authenticity of a public key is needed in this scheme to avoid spoofing by adversary as the receiver. With a public key cryptosystem, the key used to encipher a message can be made public without compromising the secrecy of a different key needed to decipher that message. Asymmetric cryptography , also known as public key cryptography, refers to a cryptographic algorithm which requires two separate keys, one of which is private and one of which is public. Public key algorithms rely on one key for encryption and a different but related key for decryption. these algorithms have the following important characteristics:. However, public key encryption has proved indispensable for key management, for distributing the keys needed for the more traditional symmetric key encryption decryption of the content, for digital signature applications, etc.
Comments are closed.