Cross Site Scripting Open Bug Bounty Blog

Cross Site Scripting Open Bug Bounty Blog Cross site scripting, commonly known as xss, remains one of the most prevalent and dangerous security vulnerabilities. in this blog post, we will delve into the different types of xss, explore how it can be exploited, and learn how to detect and mitigate it, all while…. A collection of cross site scripting (xss) writeups and reports from world best hackers. in this blog you will see 50 disclosed reports.

Open Bug Bounty How It Works Pdf Vulnerability Computing Recently, i discovered a cross site scripting (xss) vulnerability in a prominent platform, and i’m here to share my journey — from detection to reporting — that led to a rewarding outcome. Cross site scripting (xss) attacks are a type of injection, in which malicious scripts are injected into websites. there is 3 types of xss attack: a type of xss that has payloads found in the dom rather than within the html code. this vulnerability can appear in all features of the application. In this article, i created a resource for you to get better information about xss. there are many xss bypass payloads in this resource, and there are a lot of technical sources. i hope that will be useful. Cross site scripting (xss) attacks are a type of injection, in which malicious scripts are injected into websites. there is 3 types of xss attack: a type of xss that has payloads found in the dom rather than within the html code. this vulnerability can appear in all features of the application.

Bugbounty Open Bug Bounty Blog In this article, i created a resource for you to get better information about xss. there are many xss bypass payloads in this resource, and there are a lot of technical sources. i hope that will be useful. Cross site scripting (xss) attacks are a type of injection, in which malicious scripts are injected into websites. there is 3 types of xss attack: a type of xss that has payloads found in the dom rather than within the html code. this vulnerability can appear in all features of the application. 28906 cross site scripting vulnerability report id: obb 3047203 security researcher xav0 , a holder of 5 badges for responsible and coordinated disclosure, found cross site scripting security vulnerability affecting 28906 website and its users. Finding cross site scripting (xss) vulnerabilities in bug bounty program. finding xss in bug bounty program can be hard at first, so i have wrote some things together to do have a. Received 74 recommendations , a holder of 9 badges for responsible and coordinated disclosure, found cross site scripting security vulnerability affecting terminal lugs website and its users. following the coordinated and responsible vulnerability disclosure guidelines of the iso 29147 standard, open bug bounty has:. You can utilize these urls to trigger xss when a site allows url input from users. a site might allow the user to load an image by using a url and use it as their profile picture, like this:.

Cross Site Scripting Xss Github Bug Bounty 28906 cross site scripting vulnerability report id: obb 3047203 security researcher xav0 , a holder of 5 badges for responsible and coordinated disclosure, found cross site scripting security vulnerability affecting 28906 website and its users. Finding cross site scripting (xss) vulnerabilities in bug bounty program. finding xss in bug bounty program can be hard at first, so i have wrote some things together to do have a. Received 74 recommendations , a holder of 9 badges for responsible and coordinated disclosure, found cross site scripting security vulnerability affecting terminal lugs website and its users. following the coordinated and responsible vulnerability disclosure guidelines of the iso 29147 standard, open bug bounty has:. You can utilize these urls to trigger xss when a site allows url input from users. a site might allow the user to load an image by using a url and use it as their profile picture, like this:.
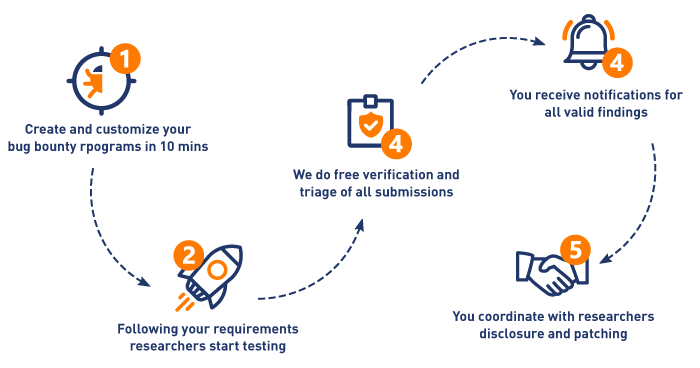
About The Project Open Bug Bounty Website Vulnerabilities Received 74 recommendations , a holder of 9 badges for responsible and coordinated disclosure, found cross site scripting security vulnerability affecting terminal lugs website and its users. following the coordinated and responsible vulnerability disclosure guidelines of the iso 29147 standard, open bug bounty has:. You can utilize these urls to trigger xss when a site allows url input from users. a site might allow the user to load an image by using a url and use it as their profile picture, like this:.
Bug Bounty Methodology Cross Site Scripting Md At Main Trilokdhaked
Comments are closed.