Course1 Task3 1 Pdf Public Key Cryptography Cryptography

Public Key Cryptography Pdf Public Key Cryptography Key Pkc stands for public key cryptography. it is also known as asymmetric cryptography. it is an encryption technique or a framework that uses a pair of keys (public and private key) for secure data communication. these keys are related, but not identical keys. Public key encryption means the algorithm has two keys: one public and one private. in this section, we explore public key encryption and the rsa encryption algorithm, named after the algorithm's inventors ron rivest, adi shamir, and len adleman.

Lecture 05 Public Key Cryptography And Rsa Pdf Cryptography Public key two key asymmetric cryptography involves the use of two keys: a public key, which may be known by anybody, and can be used to encrypt messages, and verify signatures. Reduce protection of information to protection of authenticity of public keys • no need to keep public keys secret, but must be sure that alice’s public key is really her true public key. Programming assignments and quizzes from all courses within the blockchain specialization offered by the university at buffalo and the state university of new york and key takeaways from study and research of myself. Unit iii 1 free download as pdf file (.pdf), text file (.txt) or read online for free.

An Introduction To Public Key Cryptography And Its Common Applications Programming assignments and quizzes from all courses within the blockchain specialization offered by the university at buffalo and the state university of new york and key takeaways from study and research of myself. Unit iii 1 free download as pdf file (.pdf), text file (.txt) or read online for free. To generate e, d and n to meet req 1.: how complex is rsa to calculate ciphertext and plaintext? factoring large numbers is hard, but improvements in factoring algorithms and computer speeds, makes it easier. Each receiver possesses a unique decryption key, generally referred to as his private key. receiver needs to publish an encryption key, referred to as his public key. some assurance of the authenticity of a public key is needed in this scheme to avoid spoofing by adversary as the receiver. However, public key encryption has proved indispensable for key management, for distributing the keys needed for the more traditional symmetric key encryption decryption of the content, for digital signature applications, etc. Each key pair consists of a public key and a corresponding private key. [1][2] key pairs are generated with cryptographic algorithms based on mathematical problems termed one way functions. security of public key cryptography depends on keeping the private key secret; the public key can be openly distributed without compromising security. [3].

Public Key Cryptography To generate e, d and n to meet req 1.: how complex is rsa to calculate ciphertext and plaintext? factoring large numbers is hard, but improvements in factoring algorithms and computer speeds, makes it easier. Each receiver possesses a unique decryption key, generally referred to as his private key. receiver needs to publish an encryption key, referred to as his public key. some assurance of the authenticity of a public key is needed in this scheme to avoid spoofing by adversary as the receiver. However, public key encryption has proved indispensable for key management, for distributing the keys needed for the more traditional symmetric key encryption decryption of the content, for digital signature applications, etc. Each key pair consists of a public key and a corresponding private key. [1][2] key pairs are generated with cryptographic algorithms based on mathematical problems termed one way functions. security of public key cryptography depends on keeping the private key secret; the public key can be openly distributed without compromising security. [3].
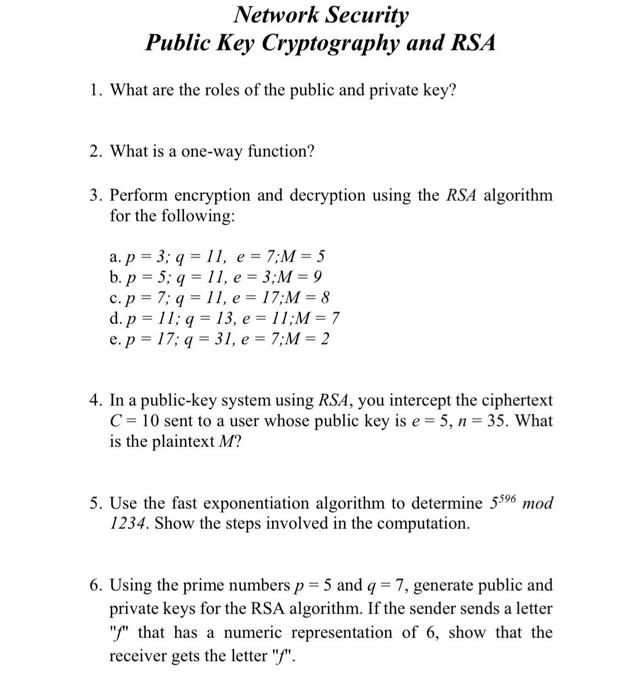
Solved Network Security Public Key Cryptography And Rsa 1 Chegg However, public key encryption has proved indispensable for key management, for distributing the keys needed for the more traditional symmetric key encryption decryption of the content, for digital signature applications, etc. Each key pair consists of a public key and a corresponding private key. [1][2] key pairs are generated with cryptographic algorithms based on mathematical problems termed one way functions. security of public key cryptography depends on keeping the private key secret; the public key can be openly distributed without compromising security. [3].

Public Key Cryptography Pdf Public Key Cryptography Key
Comments are closed.