Containers Security And Risks Within Containerized Environments

Containers Security And Risks Within Containerized Environments Explore the security risks associated with containers and learn how to secure your containerized environments. This article has offered insight into container security by describing areas companies should secure, common challenges and risks to face, and best practices to secure containerized environments.

Containerization Technology Security Best Practices To Protect As the adoption of containers as a service among organizations rises, microsoft threat intelligence continues to monitor the unique security threats that affect containerized environments. Understand the top container security risks in this insightful article, highlighting vulnerabilities, risks and threats attacking containers. Learn 10 container security best practices. discover critical strategies to safeguard applications and protect ci cd pipelines from vulnerabilities. Explore common container security risks and best practices to protect your infrastructure, applications, and sensitive data in containerized environments.

Security Best Practices For Containerized Environments Learn 10 container security best practices. discover critical strategies to safeguard applications and protect ci cd pipelines from vulnerabilities. Explore common container security risks and best practices to protect your infrastructure, applications, and sensitive data in containerized environments. This comprehensive article aims to explore the security risks associated with containerized applications in detail, analyzing various aspects side by side for effective understanding. There are several reasons why securing containers can present unique challenges, including: containers are less familiar to traditional companies that still use on prem technology and have lower availability of skills compared to older technologies. container technologies come with no out of the box security and require significant hardening. Learn from real world incidents like the docker hub breach and tesla kubernetes cluster breach, and uncover essential strategies to fortify your containerized environments against evolving threats. Effective container security focuses on minimizing vulnerabilities in container images, securing registries and orchestration platforms, enforcing strict access controls, and monitoring runtime environments for anomalies.

Container Security Concept App Security Practice Of Protecting This comprehensive article aims to explore the security risks associated with containerized applications in detail, analyzing various aspects side by side for effective understanding. There are several reasons why securing containers can present unique challenges, including: containers are less familiar to traditional companies that still use on prem technology and have lower availability of skills compared to older technologies. container technologies come with no out of the box security and require significant hardening. Learn from real world incidents like the docker hub breach and tesla kubernetes cluster breach, and uncover essential strategies to fortify your containerized environments against evolving threats. Effective container security focuses on minimizing vulnerabilities in container images, securing registries and orchestration platforms, enforcing strict access controls, and monitoring runtime environments for anomalies.
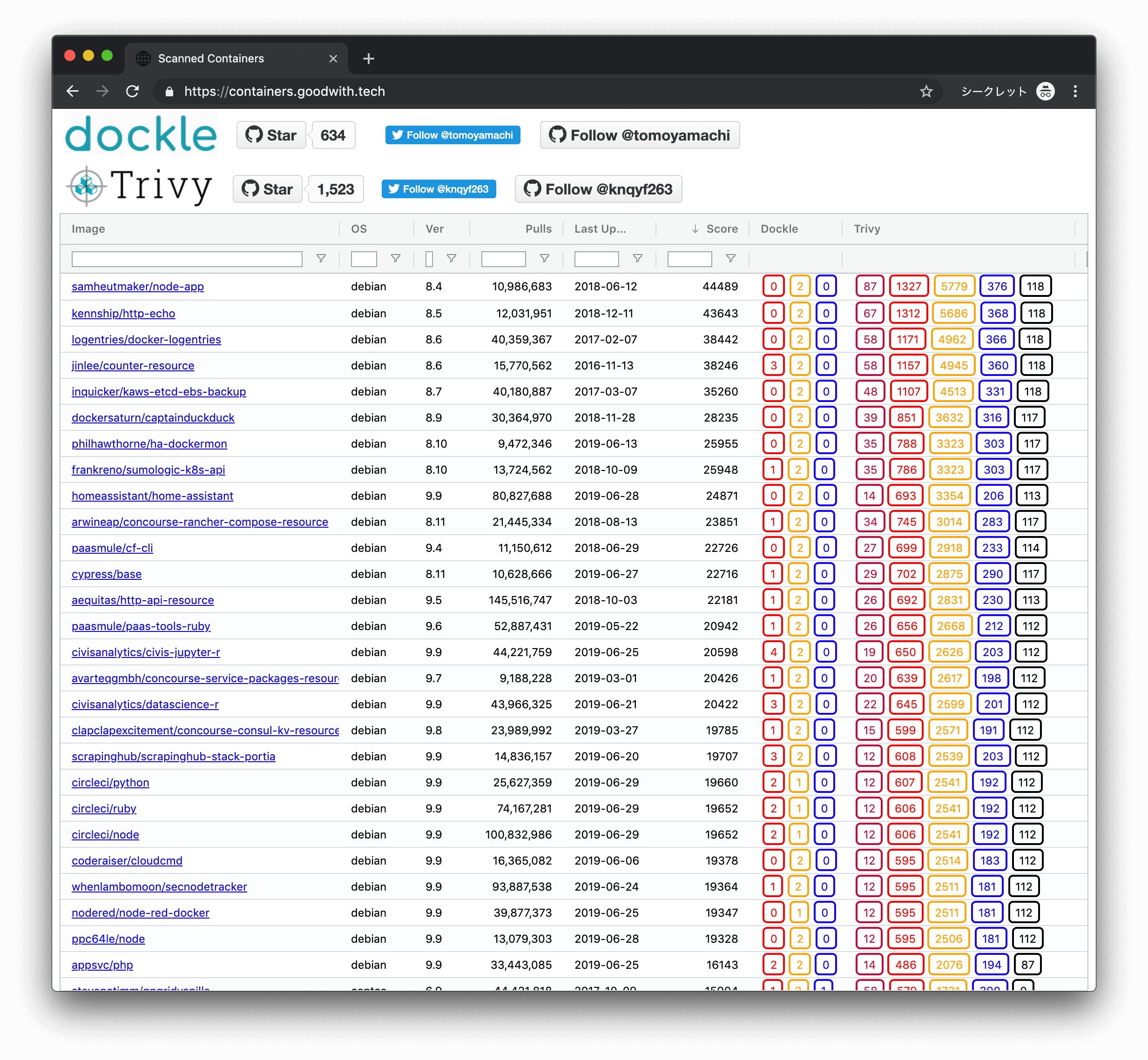
Security Issues In Popular Containers Learn from real world incidents like the docker hub breach and tesla kubernetes cluster breach, and uncover essential strategies to fortify your containerized environments against evolving threats. Effective container security focuses on minimizing vulnerabilities in container images, securing registries and orchestration platforms, enforcing strict access controls, and monitoring runtime environments for anomalies.

Containers Security Issues Challenges And Road Ahead Pdf
Comments are closed.