Can You Decrypt A Hashed Password Shorts Encryption Hashing Password

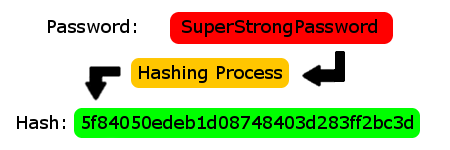
Hashing Vs Encryption How Your Password Is Being Stored In Server Hashed passwords can’t be decrypted. the hashing functions are not reversible, so there is no way to directly get back a password from its hashed representation. The principle of hashing is not to be reversible, there is no decryption algorithm, that's why it is used for storing passwords: it is stored encrypted and not unhashable. example: 123 456=579, from 579 how to find 123 and 456? this is not possible except by trying all possible combinations.

Can You Decrypt A Hashed Password Shorts Encryption Hashing Hashing is a one way function, meaning that once you hash a password it is very difficult to get the original password back from the hash. encryption is a two way function, where it's much easier to get the original text back from the encrypted text. With encryption, you can decrypt the enciphered text to retrieve he original plaintext. with hashing, you don't need to retrieve the original plaintext. however, you can verify whether or not the subsequent hashed text matches the original hashed text. example: i, a legitimate user, choose my password as "password". Once you have a hash, you can only guess the original password via a brute force attack, which involves hashing a variety of possible passwords until you end up with the same hash value, which indicates that the password you guessed is the same as the original. Because hashing is a one way function (i.e., it is impossible to "decrypt" a hash and obtain the original plaintext value), it is the most appropriate approach for password validation. even if an attacker obtains the hashed password, they cannot use it to log in as the victim.
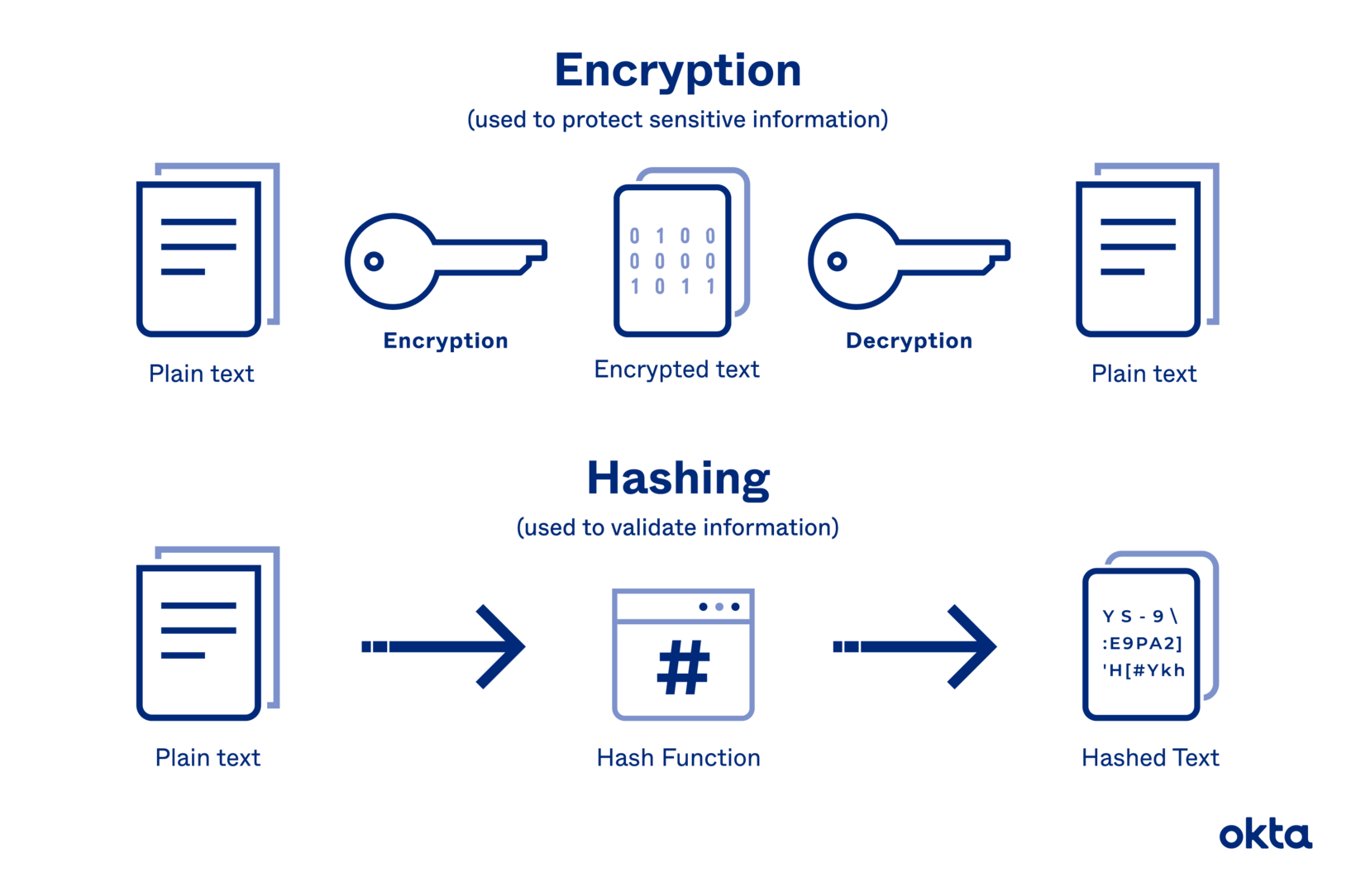
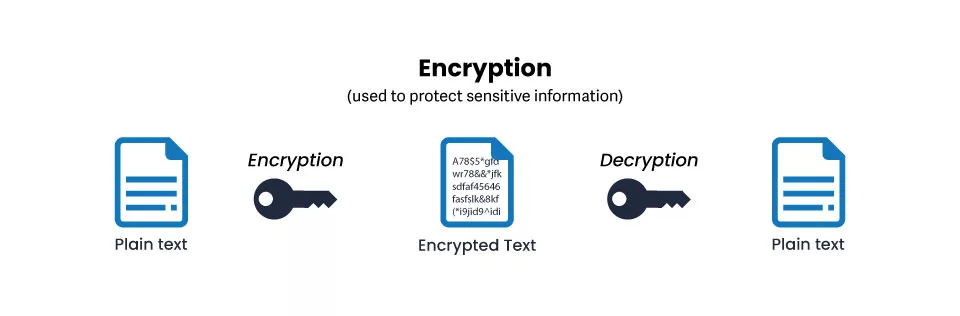
Hashing Vs Encryption Definitions Differences Okta Once you have a hash, you can only guess the original password via a brute force attack, which involves hashing a variety of possible passwords until you end up with the same hash value, which indicates that the password you guessed is the same as the original. Because hashing is a one way function (i.e., it is impossible to "decrypt" a hash and obtain the original plaintext value), it is the most appropriate approach for password validation. even if an attacker obtains the hashed password, they cannot use it to log in as the victim. You cannot dehash, reverse, or decrypt password hashes. these words confuse a key concept of how password attacks work. use 'cracking' instead. this is why. Hashing is a one way process, meaning it’s irreversible: once a password has been hashed, you can’t access, interpret, or reverse engineer the original text. Encryption: converts data into a secure format that can only be accessed with a decryption key. it protects data in transit and at rest. hashing: transforms data into a fixed size string of characters and is commonly used for verifying data integrity and securely storing passwords. Password encryption uses an algorithm and an encryption key, which is a randomized string of bits, to turn plaintext (e.g., a readable password) into an unreadable format. when a login or file access later occurs, the encryption key is used to decrypt the data and reverse it into a readable format.

Difference Between Encryption And Hashing Salt Cryptography You cannot dehash, reverse, or decrypt password hashes. these words confuse a key concept of how password attacks work. use 'cracking' instead. this is why. Hashing is a one way process, meaning it’s irreversible: once a password has been hashed, you can’t access, interpret, or reverse engineer the original text. Encryption: converts data into a secure format that can only be accessed with a decryption key. it protects data in transit and at rest. hashing: transforms data into a fixed size string of characters and is commonly used for verifying data integrity and securely storing passwords. Password encryption uses an algorithm and an encryption key, which is a randomized string of bits, to turn plaintext (e.g., a readable password) into an unreadable format. when a login or file access later occurs, the encryption key is used to decrypt the data and reverse it into a readable format.
Password Hashing Encryption: converts data into a secure format that can only be accessed with a decryption key. it protects data in transit and at rest. hashing: transforms data into a fixed size string of characters and is commonly used for verifying data integrity and securely storing passwords. Password encryption uses an algorithm and an encryption key, which is a randomized string of bits, to turn plaintext (e.g., a readable password) into an unreadable format. when a login or file access later occurs, the encryption key is used to decrypt the data and reverse it into a readable format.
Hashing Vs Encryption Know Their Real Differences
Comments are closed.