Bypass Vpns To Track A Mac With Arduino Tutorial

Source Arduino Bypass But what if a hacker or pentester could bypass a vpn's ability to hide a device's location using the wi fi networks around them? today, on cyber weapons lab, we'll explore that possibility. In this third installment on hacking with arduino, we'll be pulling out all the stops for tracking a macos computer. the payload we're going to be using will take advantage of tools built into macos to send tracking information to a remote server, allowing us to see both the ip address and location of the computer being followed.
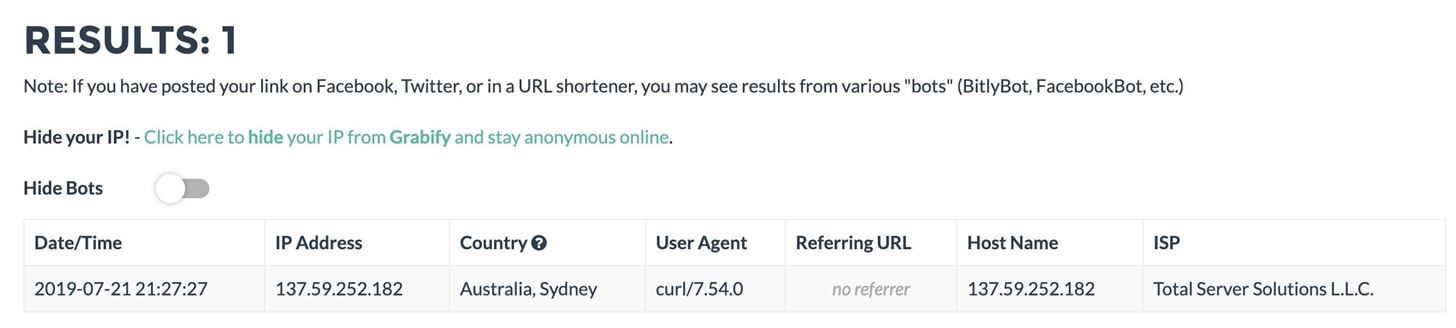
How To Hack With Arduino Defeat Vpns Track A Macos Computer Remotely But what if a hacker or pentester could bypass a vpn's ability to hide a device's location using the wi fi networks around them? today, on cyber weapons lab, we'll explore that possibility with our third installment of hacking with arduino. I've read many blogs and found there is a lot of great information scattered all around but no convenient one stop shop for those who are interested in producing their own, quality, working device with a step by step tutorial. Vpns are important for maintaining online privacy. but what if a hacker or pentester could bypass a vpn's ability to hide a device's location using the wi fi networks around them?. In this lab, you will learn the end to end process of bypassing mac address filtering. you will first identify a target network, find the mac address of an already authorized client, and then change your own wireless adapter's mac address to impersonate that client.

How To Hack With Arduino Defeat Vpns Track A Macos Computer Remotely Vpns are important for maintaining online privacy. but what if a hacker or pentester could bypass a vpn's ability to hide a device's location using the wi fi networks around them?. In this lab, you will learn the end to end process of bypassing mac address filtering. you will first identify a target network, find the mac address of an already authorized client, and then change your own wireless adapter's mac address to impersonate that client. With an arduino based attack, we'll use a five dollar setup to inject a rogue wi fi network and steal the list of trusted wi fi networks, allowing us to see where the computer has been. Today, we'll show you how a hacker or pentester could extract a macbook's network list, on this episode of cyber weapons lab. Arduino mac maker keeps a track of each of your arduinos by task and holds all of the information, network address, mac address, routing details etc so you can just copy and paste the header into your sketch for use. But what if a hacker or pentester could bypass a vpn's ability to hide a device's location using the wi fi networks around them? today, on cyber weapons lab, we'll explore that possibility with our third installment of hacking with arduino.
Comments are closed.