Authentication Authorization Protocols Oauth Vs Openi Vrogue Co
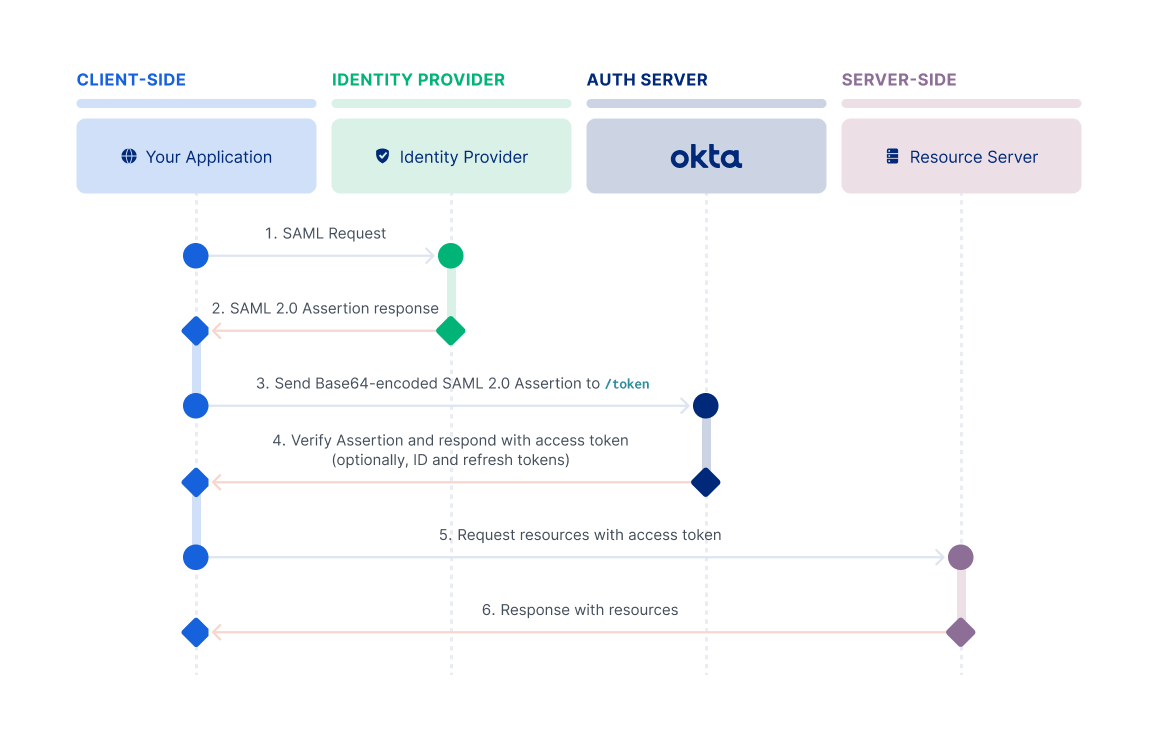
Authentication Authorization Protocols Oauth Vs Openi Vrogue Co Oauth is best for controlling access to resources, while openid connect adds user authentication. choosing the right protocol depends on whether the application needs authorization only or both identity and authorization. Oauth 2.0 and openid connect represent two of the most widely adopted security protocols, each serving distinct yet complementary purposes in the identity and access management ecosystem[3][4].

Authentication Authorization Protocols Oauth Vs Openid Connect Vs Saml Explore the key differences between oauth 2.0 and openid connect for identity management, and learn why choosing the right protocol. Understand the difference between openid and oauth oauth2. learn key differences between these api security protocols, when to use each, and how they work together. Understanding oauth vs openid connect is crucial for anyone looking to implement secure user authentication and authorization in their applications. this guide clearly explains each protocol, highlighting their key differences and practical uses. Oidc uses the oauth flow to securely perform its authentication handshake. oauth 2.1 isn’t a radical rewrite of the protocol. instead, think of it as a consolidation and security first simplification.
Authentication Authorization Protocols Oauth Vs Openid Connect Vs Saml Understanding oauth vs openid connect is crucial for anyone looking to implement secure user authentication and authorization in their applications. this guide clearly explains each protocol, highlighting their key differences and practical uses. Oidc uses the oauth flow to securely perform its authentication handshake. oauth 2.1 isn’t a radical rewrite of the protocol. instead, think of it as a consolidation and security first simplification. While both protocols share some similarities, they differ significantly in their design, functionality, and use cases. in this blog post, we will delve into the intricacies of oauth 2.0 and openid connect, exploring the differences between the two and providing guidance on when to use each. This makes it essential for businesses, cloud professionals, and security experts to grasp the nuances of key authentication protocols—saml, openid connect, and oauth. Oauth 2.0 was intentionally designed to provide authorization without providing user identity and authentication, as those problems have very different security considerations that don’t necessarily overlap with those of an authorization protocol. Here’s where it gets interesting: while oauth 2.0 handles the “what can you access” part, openid connect handles the “who are you” part. it’s like having a bouncer who not only checks if you can enter the club but also remembers your name for next time.
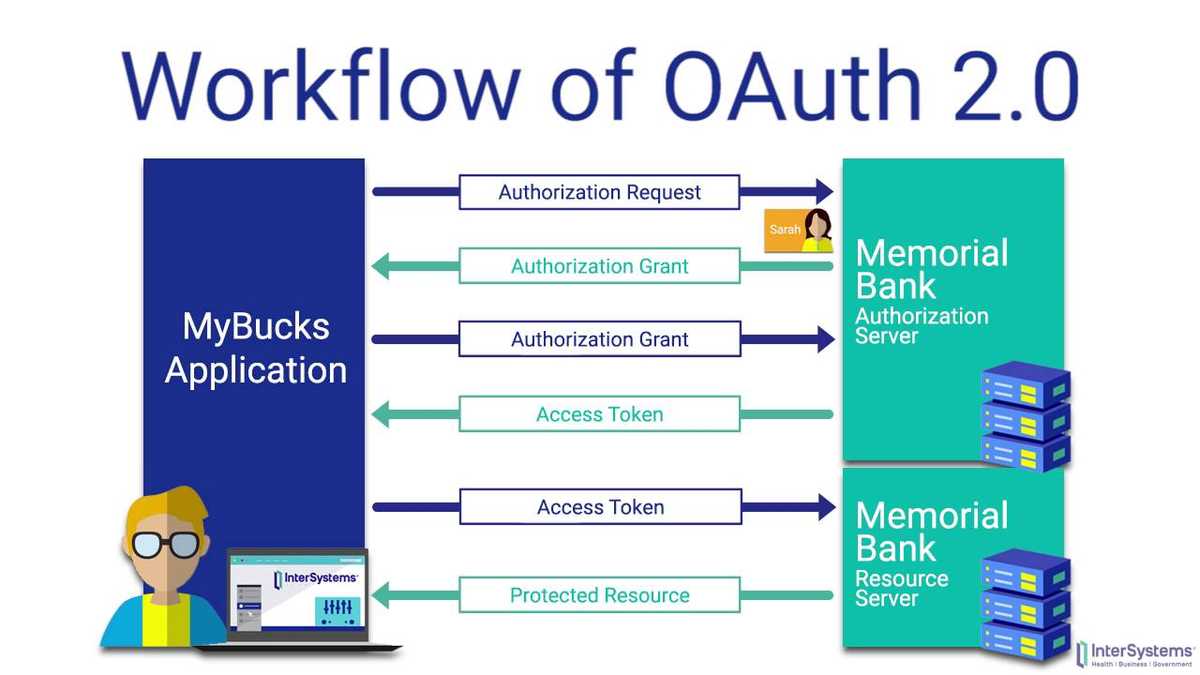
Oauth 2 0 Authorization Framework Www Vrogue Co While both protocols share some similarities, they differ significantly in their design, functionality, and use cases. in this blog post, we will delve into the intricacies of oauth 2.0 and openid connect, exploring the differences between the two and providing guidance on when to use each. This makes it essential for businesses, cloud professionals, and security experts to grasp the nuances of key authentication protocols—saml, openid connect, and oauth. Oauth 2.0 was intentionally designed to provide authorization without providing user identity and authentication, as those problems have very different security considerations that don’t necessarily overlap with those of an authorization protocol. Here’s where it gets interesting: while oauth 2.0 handles the “what can you access” part, openid connect handles the “who are you” part. it’s like having a bouncer who not only checks if you can enter the club but also remembers your name for next time.
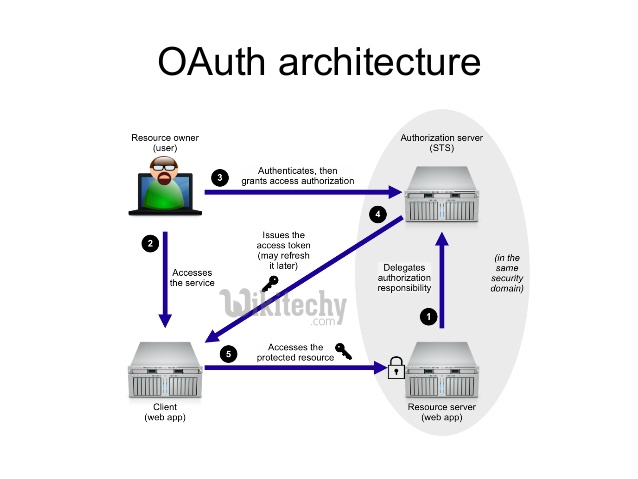
Oauth Authorization Vs Authentication Stack Overflow Oauth 2.0 was intentionally designed to provide authorization without providing user identity and authentication, as those problems have very different security considerations that don’t necessarily overlap with those of an authorization protocol. Here’s where it gets interesting: while oauth 2.0 handles the “what can you access” part, openid connect handles the “who are you” part. it’s like having a bouncer who not only checks if you can enter the club but also remembers your name for next time.
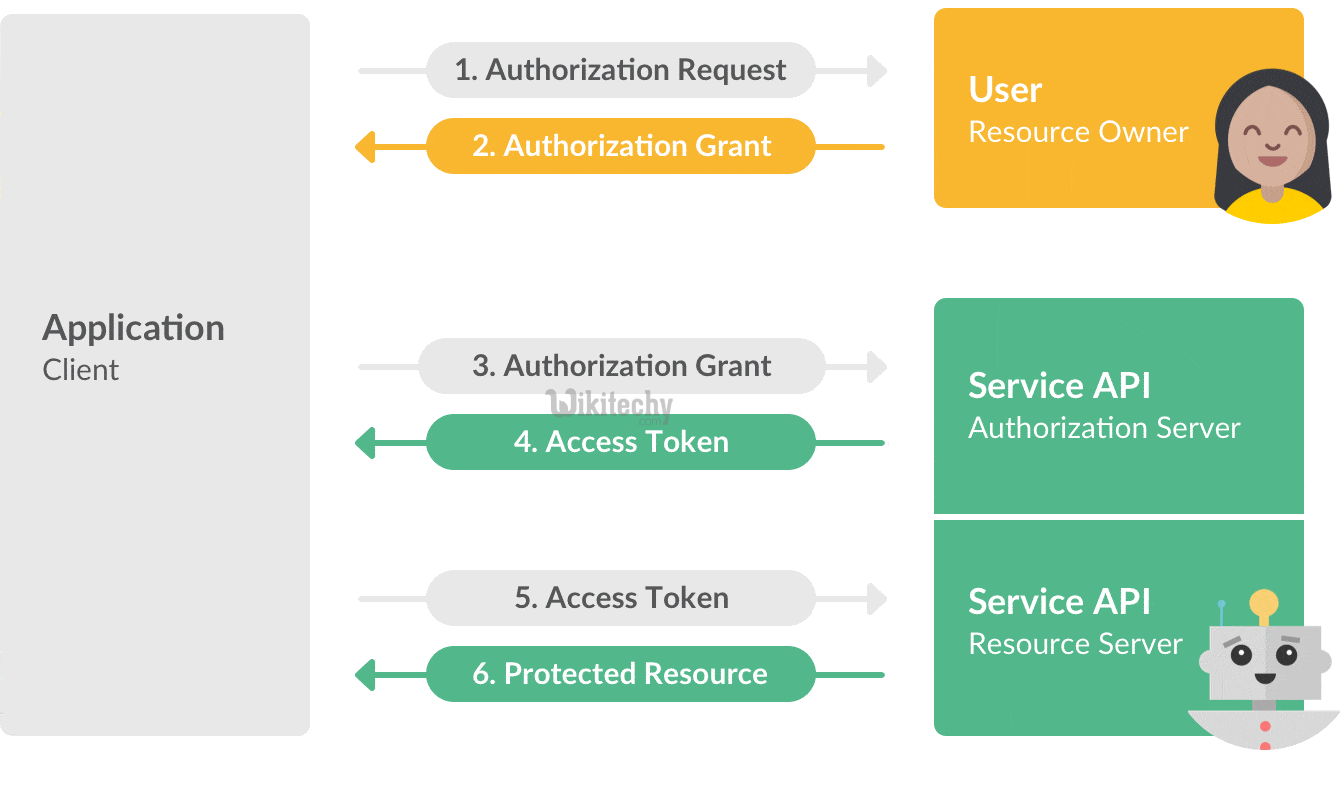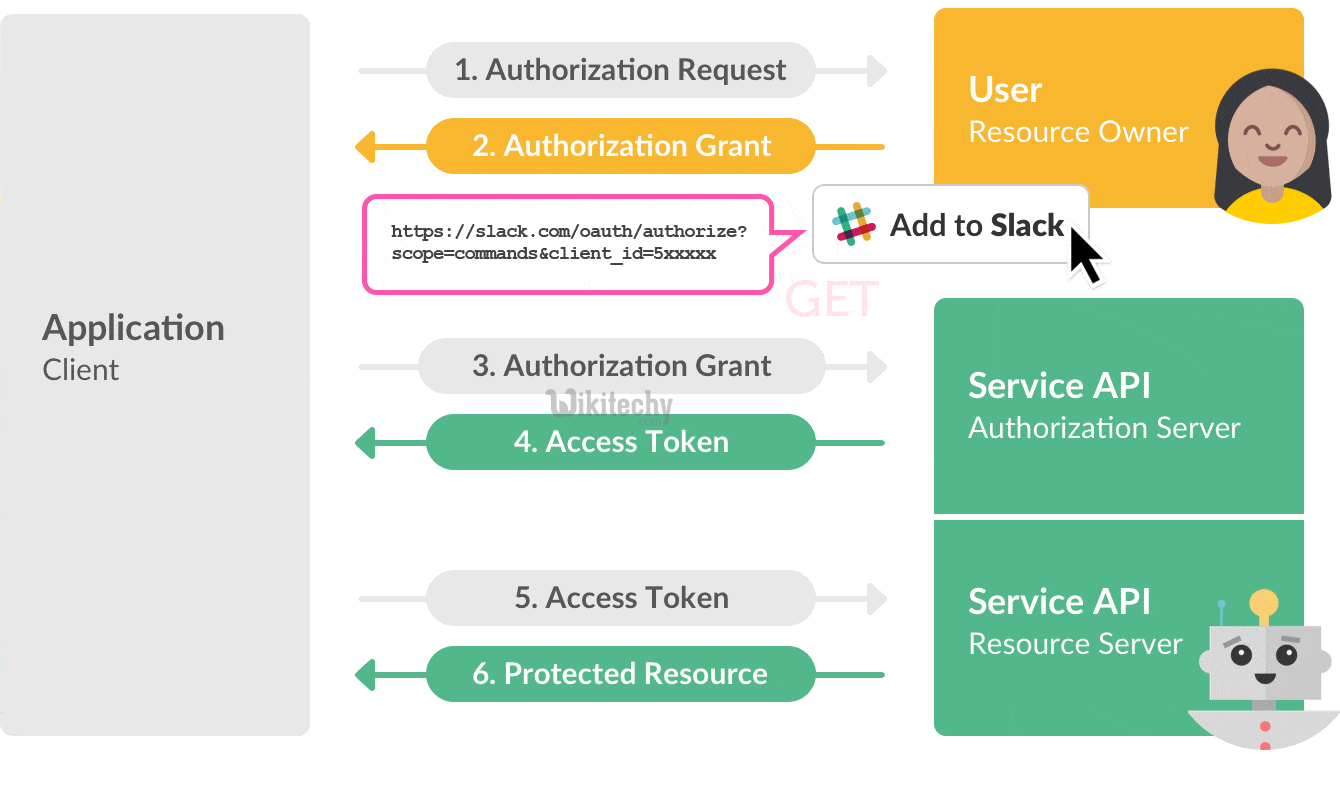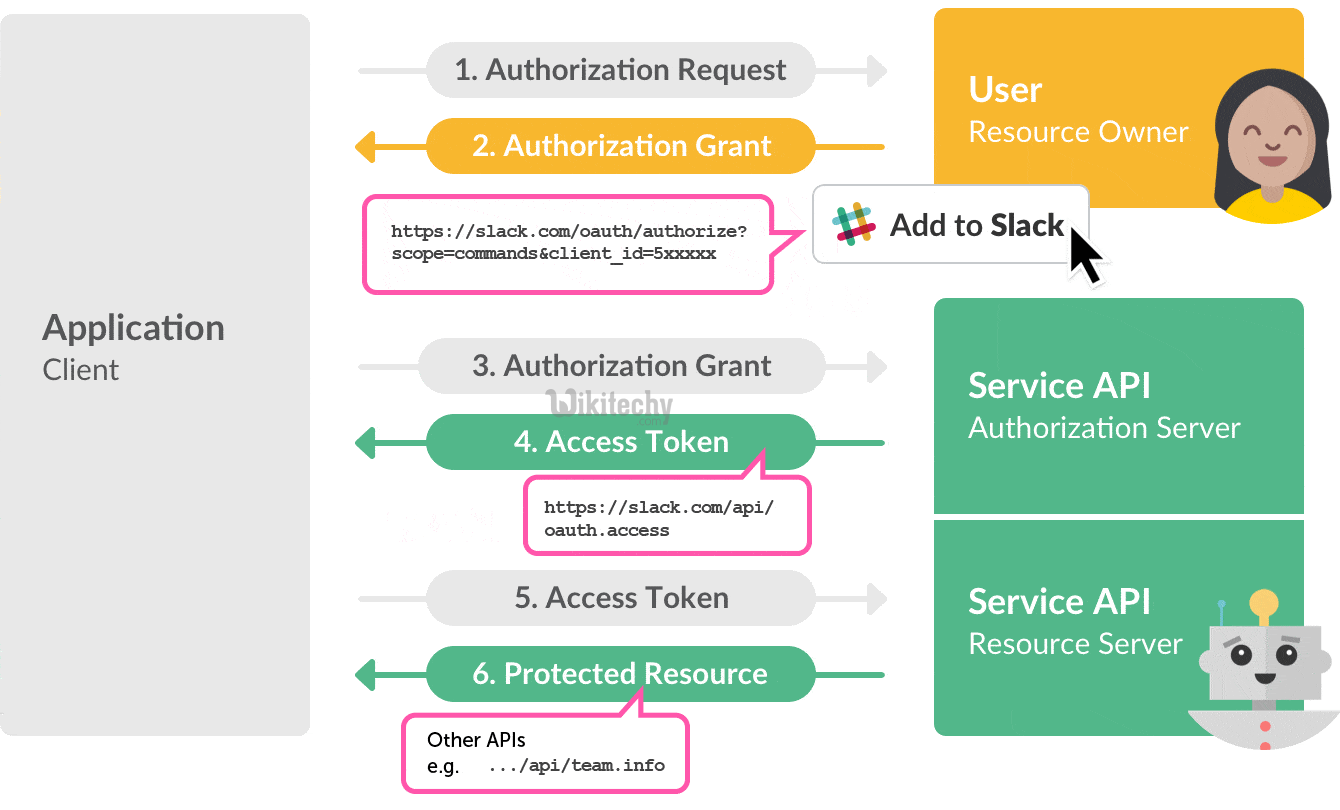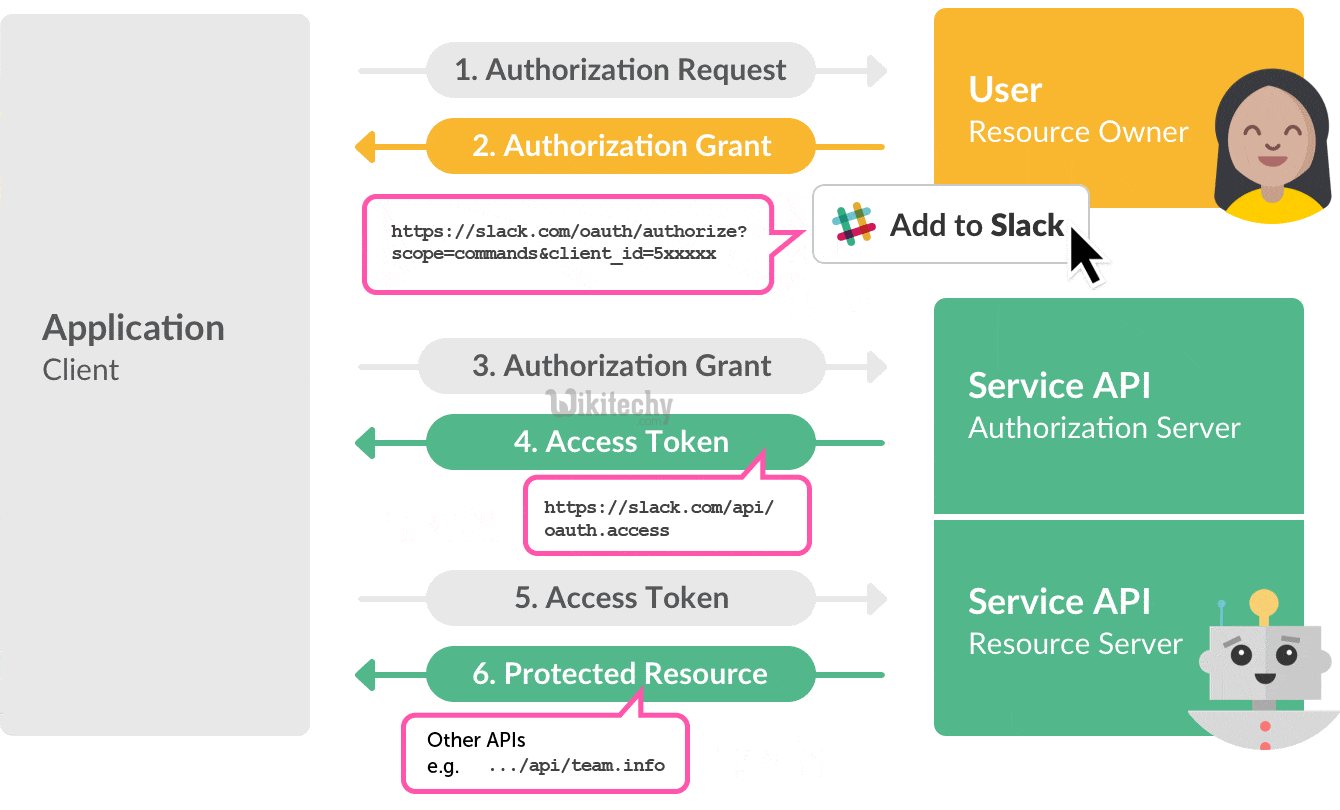
Oauth Authorization Vs Authentication Stack Overflow
Comments are closed.