Attacking Web Apps Fuzzing With Ffuf Grey Hat Developer
Attacking Web Apps Fuzzing With Ffuf Grey Hat Developer Ffuf can fuzz these urls very quickly but if we want to go even faster we can increase the number of threads being used: t 200 = number of threads to 200 however, this isn't recommended because this can disrupt the site causing a dos or possibly even bring down your own internet. In this module we will mainly focus on the ffuf tool for web fuzzing, as it is one of the most common and reliable tools available for web fuzzing. the following topics will be discussed:.

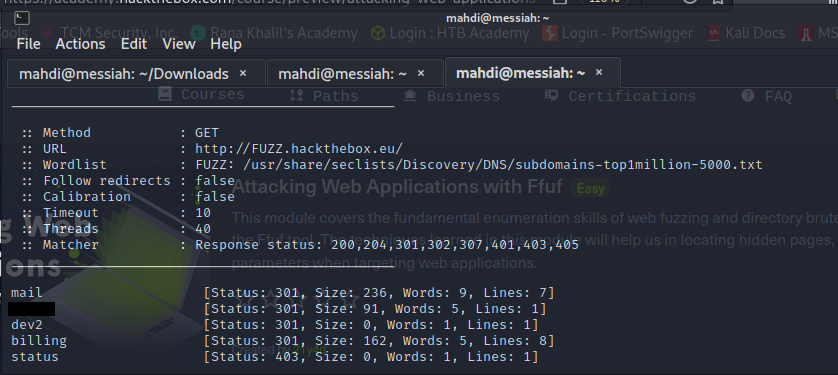
Attacking Web Apps Fuzzing With Ffuf Grey Hat Developer To scan for vhosts, without manually adding the entire wordlist to our etc hosts, we will be fuzzing http headers, specifically the "host: header". to do that, we can use the h flag to specify a header and will use the fuzz keyword within it. question: try running a vhost fuzzing scan on 'academy.htb', and see what other vhosts you get. Question 2 before you run your page fuzzing scan, you should first run an extension fuzzing scan. what are the different extensions accepted by the domains? first added newly found subdomains:. This weeks write up is on the module “ attacking web apps with ffuf”. so, without further ado, let’s get into it: whether you’re running your attack machine locally via your kali vm or. This repository demonstrates the use of ffuf, a web fuzzing tool, to identify vulnerabilities in web applications. techniques covered include directory fuzzing, page fuzzing, recursive fuzzing, sub domain fuzzing, vhost fuzzing, parameter fuzzing, and value fuzzing.

Attacking Web Apps Fuzzing With Ffuf Grey Hat Developer This weeks write up is on the module “ attacking web apps with ffuf”. so, without further ado, let’s get into it: whether you’re running your attack machine locally via your kali vm or. This repository demonstrates the use of ffuf, a web fuzzing tool, to identify vulnerabilities in web applications. techniques covered include directory fuzzing, page fuzzing, recursive fuzzing, sub domain fuzzing, vhost fuzzing, parameter fuzzing, and value fuzzing. Fuzzing refers to throwing semi random or unexpected input at an application to trigger unusual behaviors that may point to vulnerabilities. for websites specifically, this may involve tampering with urls, submitting unusual form data, adding parameters to requests etc. There are many tools and methods to utilize for directory and parameter fuzzing brute forcing. in this module we will mainly focus on the ffuf tool for web fuzzing, as it is one of the most common and reliable tools available for web fuzzing. the following topics will be discussed:.
Comments are closed.