Api Keys Definition Security Best Practices Cequence

Api Protection Best Practices Webinar Series Cequence Security Learn more about api keys, including what they are, what they're used for, and the best practices for avoiding security risks. Api keys identify users and applications requesting api access but introduce security challenges. learn about proper api key security here.

Cequence Ranked As Best In Class Api Security Vendor To help keep your api keys secure, implement the following best practices. by adding restrictions, you can limit the ways an api key can be used, reducing the impact of a compromised. Learn what api keys are, how they work, their uses, types, and security best practices in software development. In simple terms, api security ensures software components maintain their connections so that private details remain secure while working securely within the cyber environment. before we delve into the practices, it is important to acknowledge the ever changing threat landscape that surrounds apis. Explore best practices for managing api keys, focusing on strategies that enhance security and support scalability for your applications and services. implement rate limiting to manage how many requests are processed by your application over a specified period.

Api Security Best Practices In simple terms, api security ensures software components maintain their connections so that private details remain secure while working securely within the cyber environment. before we delve into the practices, it is important to acknowledge the ever changing threat landscape that surrounds apis. Explore best practices for managing api keys, focusing on strategies that enhance security and support scalability for your applications and services. implement rate limiting to manage how many requests are processed by your application over a specified period. Api keys are one of the more popular ways to secure the access to a rest api. they are an easy method to grant and manage access to an api and track its usage. according to blobr’s own api portal report, 67% of the top 100 api companies use api keys, while the other 33% prefer oauth. Web api security is the application of any security best practice applied to web apis, which are prevalent in modern applications. web api security includes api access control and privacy, as well as the detection and remediation of attacks on apis through api reverse engineering and the exploitation of api vulnerabilities as described in owasp api security top 10. whether an application is. Enhance your api security with these 8 api key management best practices. learn how to protect your sensitive data and prevent unauthorized access in 2025. apis are essential for modern software. they power everything from simple mobile apps to complex ai platforms and machine learning models. From using environment variables to implementing proper access controls, encrypting your keys, and monitoring and rotating them regularly, there are plenty of best practices to help you keep your api keys safe.
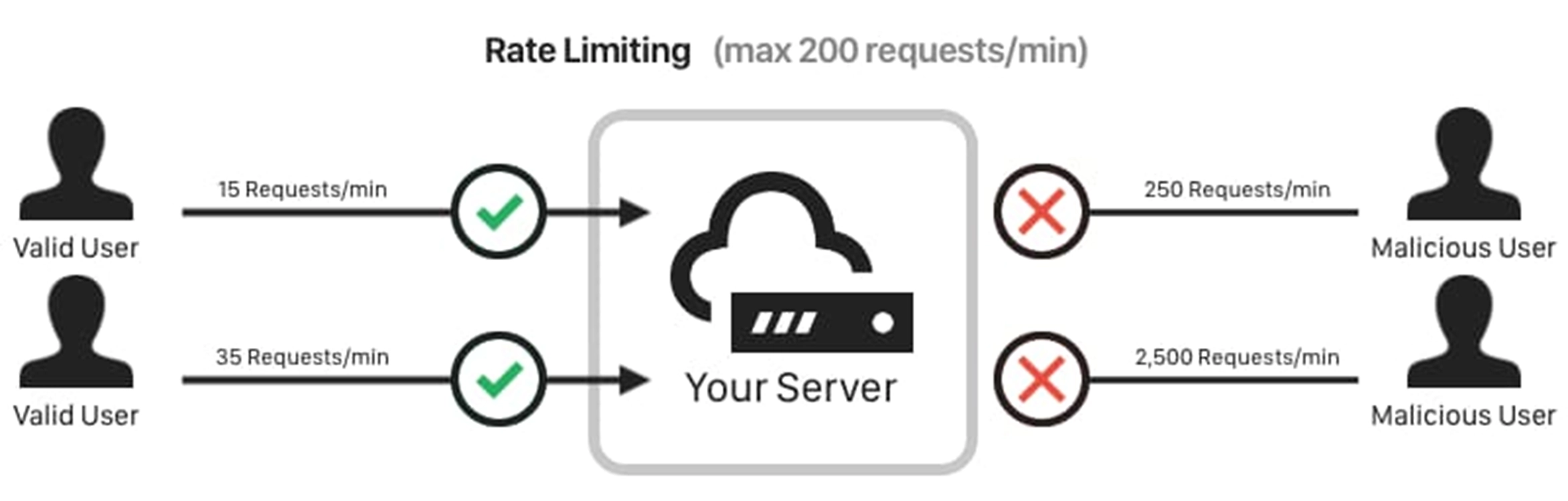
Api Keys Definition Security Best Practices Cequence Api keys are one of the more popular ways to secure the access to a rest api. they are an easy method to grant and manage access to an api and track its usage. according to blobr’s own api portal report, 67% of the top 100 api companies use api keys, while the other 33% prefer oauth. Web api security is the application of any security best practice applied to web apis, which are prevalent in modern applications. web api security includes api access control and privacy, as well as the detection and remediation of attacks on apis through api reverse engineering and the exploitation of api vulnerabilities as described in owasp api security top 10. whether an application is. Enhance your api security with these 8 api key management best practices. learn how to protect your sensitive data and prevent unauthorized access in 2025. apis are essential for modern software. they power everything from simple mobile apps to complex ai platforms and machine learning models. From using environment variables to implementing proper access controls, encrypting your keys, and monitoring and rotating them regularly, there are plenty of best practices to help you keep your api keys safe.
Comments are closed.