Analysis Of Ctf Detection In The Last 7th Operation Of The 5th Tool

Analysis Of Ctf Detection In The Last 7th Operation Of The 5th Tool The performance of a self propelled rotary carbide tool when cutting hardened steel is evaluated in this study. Successful detection of accelerated tool wear can prevent the occurrence of ctf, so using this algorithm can provide more benefits than using only ctf detection.

Ctf Analysis Windows Hard Infiltrator S Hideout The novelty of this article is an attempt to answer these questions and propose a large set of sfs related to tool wear, but without including superfluous sfs. the analysis of the usefulness of the signal properties for the state of the cutting tool in turning was carried out on a large experiment. This paper presents a methodology aimed at the identification of a catastrophic tool failure (ctf) in turning processes based on multiple sensor monitoring. I did a writeup for malware and reverse engineering challenges published on cybertalents to improve malware analysis skills and reverse engineering. This guide was written and maintained by the osiris lab at new york university in collaboration with ctfd. in this handbook you'll learn the basics™ behind the methodologies and techniques needed to succeed in capture the flag competitions. ready? what is a ctf? thank you to our incredible contributors.
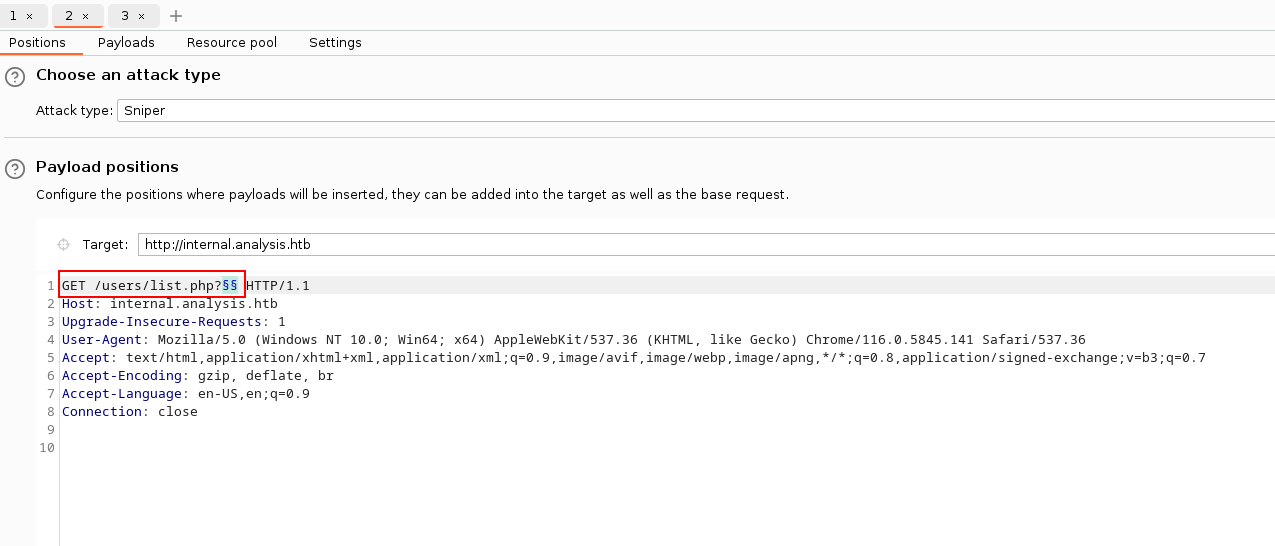
Ctf Analysis Windows Hard Infiltrator S Hideout I did a writeup for malware and reverse engineering challenges published on cybertalents to improve malware analysis skills and reverse engineering. This guide was written and maintained by the osiris lab at new york university in collaboration with ctfd. in this handbook you'll learn the basics™ behind the methodologies and techniques needed to succeed in capture the flag competitions. ready? what is a ctf? thank you to our incredible contributors. At the end of the chapter 5 (walk through of the initial level of the ctf) we are given the flag to be fed to the provided oracle binary, that will in turn generate the next level binaries, namely lvlxx. The paper presents an innovative algorithm for early detection of atw and ctf. it consists in comparing the waveforms of the cutting force sensor signal in hierarchical time windows. There are many algorithms for the identification of gradual tool wear (gtw) which usually counts in minutes and the detection of catastrophic tool failure (ctf) which counts in milliseconds. There are many algorithms for the identification of gradual tool wear (gtw) which usually counts in minutes and the detection of catastrophic tool failure (ctf) which counts in milliseconds.
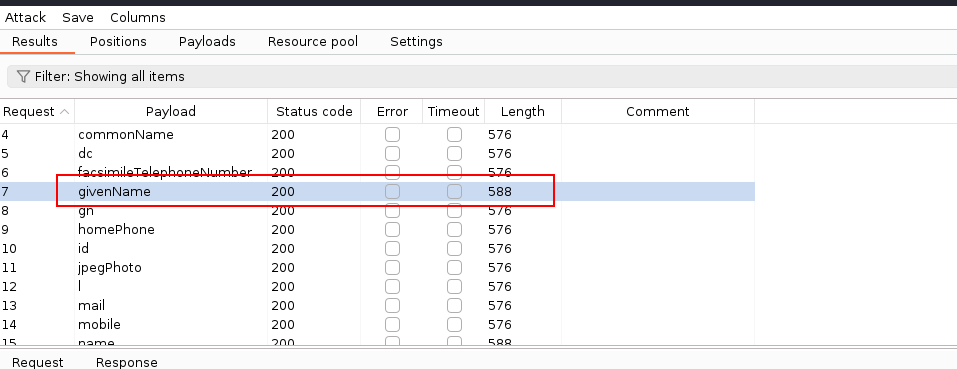
Ctf Analysis Windows Hard Infiltrator S Hideout At the end of the chapter 5 (walk through of the initial level of the ctf) we are given the flag to be fed to the provided oracle binary, that will in turn generate the next level binaries, namely lvlxx. The paper presents an innovative algorithm for early detection of atw and ctf. it consists in comparing the waveforms of the cutting force sensor signal in hierarchical time windows. There are many algorithms for the identification of gradual tool wear (gtw) which usually counts in minutes and the detection of catastrophic tool failure (ctf) which counts in milliseconds. There are many algorithms for the identification of gradual tool wear (gtw) which usually counts in minutes and the detection of catastrophic tool failure (ctf) which counts in milliseconds.
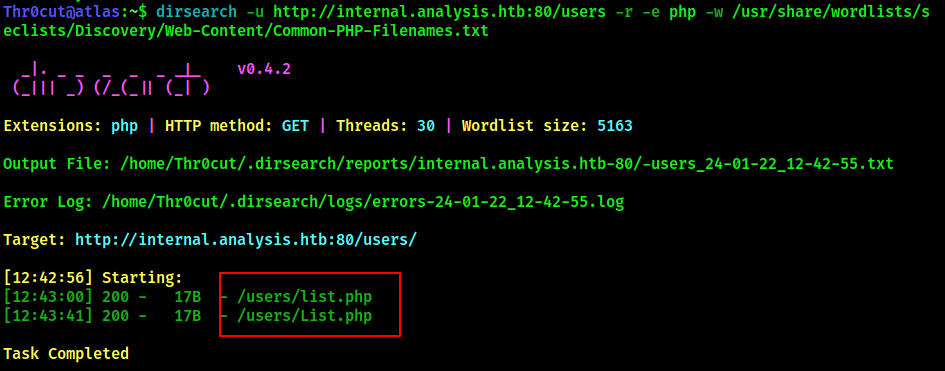
Ctf Analysis Windows Hard Infiltrator S Hideout There are many algorithms for the identification of gradual tool wear (gtw) which usually counts in minutes and the detection of catastrophic tool failure (ctf) which counts in milliseconds. There are many algorithms for the identification of gradual tool wear (gtw) which usually counts in minutes and the detection of catastrophic tool failure (ctf) which counts in milliseconds.
Comments are closed.